|
|||||||||||||||||||||
|
|
|||||||||||||||||||||
|
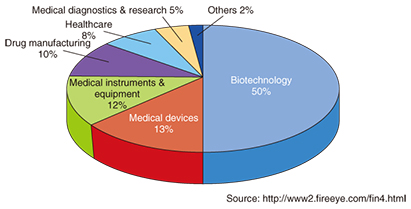
Feature Articles: Cybersecurity-related R&D to Counter Global Threats Vol. 13, No. 12, pp. 9–14, Dec. 2015. https://doi.org/10.53829/ntr201512fa2 Trends in Global Security ThreatsAbstractIn this article, to illustrate the trends in global security threats, we examine two ingenious cyber-attacks that were recently reported, and we discuss the countermeasures to the attacks. We also introduce the Global Threat Intelligence Report, an NTT Group initiative related to global security threats. We believe that sharing this sort of information about security threats will help to raise awareness of cybersecurity and lead to more secure systems. Keywords: threat information, cyber-attack, global security 1. IntroductionIn recent years, massive cyber-attacks have occurred that have inflicted damage on a scale that is difficult to assess. Examples include the JPMorgan Chase & Co. (a major American financial services firm) data breach targeting its customer information, the devastating cyber-attack on Sony Pictures that included the destruction of corporate systems and the publication of stolen corporate information, a large-scale data breach of government employee information from the United States Office of Personnel Management, and the leakage of information from Japan Pension Service. These cyber-attacks are often not reported in great detail from the viewpoint of ensuring security. However, people can strengthen the security of their own systems by using cases such as these to understand the deceptive tactics used by attackers and the measures that can be used to defeat them. Consequently, sharing information about security threats will become increasingly important in the future. In this article, we report on some sophisticated cyber-attacks reported recently, and we explain the NTT Group’s Global Threat Intelligence Report (GTIR) initiative that aims to accelerate the sharing of information. 2. FIN4: Secretly stealing confidential informationFireEye, Inc., a U.S. based network security company, analyzed certain incidents in its clients’ networks as well as data it obtained separately through their products and detected a group that is focused on secretly stealing confidential company information that could affect the stock prices of publicly traded companies. FireEye named the group FIN4. The members of this group have not been identified, so the purpose of their attacks is still unclear. However, FireEye believes that FIN4 is exploiting this insider information in order to profit on the stock market. It is very difficult to ascertain the actual damage because there have not been any apparent losses at the companies targeted in this type of cyber-attack. FIN4’s activities have been observed since mid-2013, and FireEye has discovered about 100 targets consisting of publicly traded healthcare and pharmaceutical companies (68%), firms advising public companies on matters concerning security, legal issues, and mergers & acquisitions (M&A) (20%), and other publicly traded companies (12%). For healthcare and pharmaceutical companies, information on the authorization of drugs or the development and clinical testing of new drugs can have a major impact on the share prices. Also, M&A consultants are privy to M&A information before it is made public. A breakdown of the healthcare and pharmaceutical industry sectors targeted by FIN4 is shown in Fig. 1.
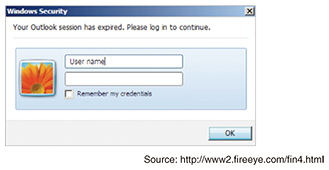
When FIN4 targets a particular company, it starts out by targeting other companies that do business with it. It then uses the email accounts of these other companies to send emails to the target company containing information on transactions that are currently in progress. These emails are addressed to people dealing with confidential information of the target company such as management executives, company attorneys, and researchers. They include attached Office*1 documents that are exchanged in actual transactions but that have embedded macros that display a fake Outlook*1 login prompt when the files are opened [1] (Fig. 2) and then send the login information to FIN4’s server. For environments where macros are disabled, the email message includes a link to a fake Outlook Web App (OWA) login page from where the login information can be stolen. Using this stolen Outlook authentication information, FIN4 accesses the email accounts of people who work with the target company’s insider information and obtains confidential information by intercepting and reading their email.
FIN4 also creates settings that automatically delete emails containing terms such as hacking, phishing, and malware from the target’s Outlook account. As a result, the targeted individual is not able to see warning emails with messages such as “Is your company being targeted?” from external correspondents. The U.S. Securities and Exchange Commission (SEC) was reported to have requested detailed reports on at least eight companies targeted by FIN4 [2], but as of the end of June 2015, they had not yet released a public statement on the issue. Steps that can be taken to avoid becoming one of FIN4’s victims include disabling macros in Microsoft Office and enabling two-factor authentication for OWA. Also, since FIN4 uses Tor*2 to conceal the traffic that sends login information to its server, another effective measure is to monitor the internal network logs to check for communication with known Tor nodes.
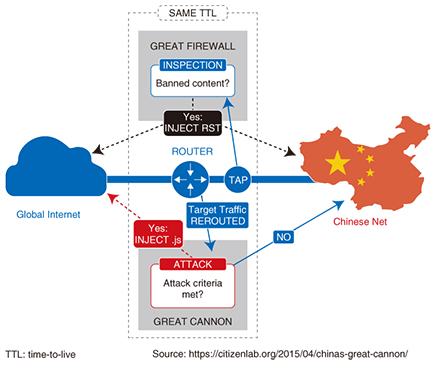
3. The Great Cannon of ChinaA study by the Citizen Lab at the University of Toronto has shown that the Great Firewall (GFW)*3 of China is now partnered with an attack system, which it calls the Great Cannon (GC). In March 2015, GreatFire.org and GitHub*4 became the first observed victims of massive DDoS (distributed denial of service) attacks from GC. In the following, we describe the GC and GFW mechanisms on which they are based, as well as a GC attack. 3.1 GFW mechanismThe GFW is shown in the upper part of Fig. 3 [3]. All Internet traffic in and out of China passes through the GFW. The traffic is intercepted at the element labeled TAP, and content that is subject to restrictions or blockades is identified at the element labeled INSPECTION. When such content has been identified, the INJECT RST part transmits RST (reset) packets, which are used when blocking communication or denying access, to the source and destination servers. A load-balancing mechanism is used in the GFW so that it can process multiple communication streams in parallel. In this way, the GFW continuously monitors network traffic in order to block access to content that the Chinese authorities regard as undesirable.
3.2 GC mechanismIn the GC, the Target Traffic REROUTED component in Fig. 3 reroutes the corresponding traffic, and the ATTACK component identifies whether or not it is to be used in an attack. If so, an attack code is sent to the access source; otherwise it connects to the requested destination server. On receiving an attack code, the access source becomes a temporary agent that supports a GC attack. Just as with the GFW, all Internet traffic in and out of China passes through the GC, so it is possible to launch a large-scale attack even when only a tiny fraction of traffic is used by the GC. The GC takes over this traffic, which makes it capable of launching man-in-the-middle (MITM) attacks. The GC is compatible with high-bandwidth communications, so it collects only IP addresses of the access sources. It also has a mechanism for caching previous traffic so that it can eliminate unnecessary work when the same process is performed repeatedly on the same traffic. Citizen Lab’s test results suggest that up to 16,000 access source IP addresses can be stored in this way. According to Citizen Lab, the results of sending traffic configured to respectively operate the GC and GFW, and the results of analyzing the responses to this traffic suggest that the GC and GFW do not share attack facilities but have their own systems. However, there are similarities in the way they rewrite data packets, so they appear to share parts of the same program code and are thought to be very closely related. The GC and GFW have similar load balancer functions and are thought to distribute traffic based on the IP addresses of access sources. A Citizen Lab survey of communication paths set up to activate the GFW and GC indicated that both are on the same destination network, so it seems that the GC and GFW are installed right next to each other [3]. In one test environment, the destination network was China Telecom, and in another test environment the destination network was China Unicom. The research done by security blogger Robert Graham suggests that the GC exists in the infrastructure of China Unicom. 3.3 Attacks on GreatFire.org and GitHubFrom March 14 to March 25, 2015, a large-scale DDoS attack was carried out against GreatFire.org, which was hit with 2.6 billion requests per hour (2500 times the usual rate). GreatFile.org provides functions that use the Amazon CloudFront CDN (content delivery network) service to bypass the GFW and allow blocked sites to be viewed. Note that the Cyberspace Administration of China has already identified GreatFire.org as a foreign anti-Chinese organization. From March 25 to April 7, 2015, GitHub was also hit by a large-scale DDoS attack, causing the site’s response times to increase several times over [4]. GreatFire.org has two GitHub repositories that provide technology to users wishing to circumvent Chinese censorship. The attack on GitHub appears to have been carried out with the aim of forcing the removal of these repositories from GitHub. The GC attacked GreatFire.org and GitHub by intercepting and redirecting traffic destined for Baidu Analytics and Baidu Advertising, which are parts of the Baidu common platform. However, not all the traffic to these sites was used in the attack. According to Citizen Lab’s observations, the majority of traffic (about 98.25%) passed through to Baidu unaffected, while the remainder (about 1.75%) was used in the attack [3]. The web requests used in the attack included page views of sites containing advertising from Baidu, so the visitors to these sites were unwittingly taking part in the attacks on GreatFire.org and GitHub. 3.4 Who built the GC?Citizen Lab considers that the GC could not have been built or used without the approval of the Chinese government, since its attacks are too overt to have been conducted without government permission. It also stated that although it is not clear why the GC was built, it may have resulted from the conflict between the activities of GreatFire.org and the Chinese Communist Party’s ideology [3]. These destructive acts may be designed not only to block access to content that the party finds undesirable but also to set an example for other organizations engaged in similar activities. 3.5 PredictionsSince the GC is evidently capable of launching attacks based on the source of Internet traffic, it is assumed to have latent capabilities for other forms of cyber-attack besides DDoS, even though they have not yet been observed. For example, it could be easily reconfigured to send malware to specific individuals that access servers in China without using encryption. Also, since the GC is a complete MITM, it could even replace attachments of an unencrypted email with malware. It is very difficult for organizations and individual users to defend themselves against attacks by the GC. However, due to the way in which the GC works, these attacks only work on unencrypted traffic, and will not work on traffic encrypted using the protocol HTTPS (Hypertext Transfer Protocol Secure) or the like. The GC can therefore be rendered less effective by promoting the encryption of traffic and content by many organizations and users.
4. GTIRThe 2015 edition of GTIR [5] was produced by NTT Innovation Institute, Inc. (NTT I3) with the cooperation of NTT Group companies (NTT Com Security, Dimension Data, Solutionary, NTT Secure Platform Laboratories, and NTT DATA). It contains detailed descriptions of the following important trends based on the analysis of about 6 billion attack events observed by the NTT Group during 2014.
5. Future prospectsThe NTT Computer Security Incident Response and Readiness Coordination Team (NTT-CERT) at NTT Secure Platform Laboratories is working to improve security throughout the NTT Group and the information network society. NTT-CERT provides consultation services on information security and also delivers security-related information. We will continue with our ongoing incident response support for NTT Group companies. We also plan to continue providing security information with the aim of expanding the global scale of our activities. References
|
|||||||||||||||||||||