|
|||||||||||
|
|
|||||||||||
|
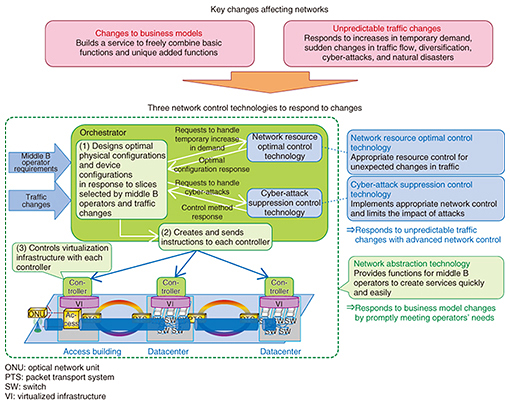
Feature Articles: Initiatives for the Widespread Adoption of NetroSphere Vol. 14, No. 10, pp. 24–30, Oct. 2016. https://doi.org/10.53829/ntr201610fa4 Network Control Technology to Realize the NetroSphere ConceptAbstractNTT has announced its NetroSphere concept, which was developed with the objective of promptly, reliably, and economically supplying services required by network users and middle B operators (the second B in the B2B2X (business-to-business-to-X) business model). NTT Network Technology Laboratories is conducting research on network control technologies to respond to the needs of diverse middle B operators flexibly and efficiently and to provide high-quality services with the aim of achieving the NetroSphere concept. This article examines the progress of these initiatives. Keywords: network configuration and control, resource optimization, security 1. IntroductionNTT has announced its NetroSphere concept [1], which is being developed in order to promptly, reliably, and economically supply services required by network users and middle B operators (service operators). In this article, we introduce three network control technologies that enable us to respond flexibly and efficiently with high-quality service to the needs of various middle B operators. These technologies consist of network abstraction to implement network design and configuration, network resource optimal control to enable responses to temporary changes in demand, and cyber-attack suppression control that achieves stable service during cyber-attacks. 2. Key changes affecting the networksFirst, the positioning and relevance of the technologies mentioned above are explained (Fig. 1). To realize the NetroSphere concept, it is necessary to respond to two kinds of changes: business models and traffic that is difficult to predict.
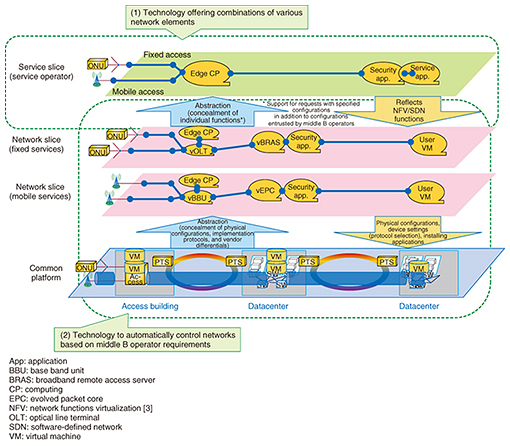
2.1 Changes to business modelsChanges to business models means shifting from a standardized supply service model where carriers provide services through individual networks such as NGN (Next Generation Network), to a B2B2X (business-to-business-to-X) business model where middle B operators can build businesses and services according to their needs by freely incorporating original value-added functions to the base functions supplied by the carriers. Accommodating these changes requires networks that can respond flexibly to various middle B operator needs and that can promptly offer services. The technology to achieve this is network abstraction technology. 2.2 Unpredictable traffic changesNetwork traffic up to now has been uniform and predictable, as service traffic has been dominated by services provided by carriers, for example, phone, Internet, and video services. However, in the NetroSphere era, we envisage an increase in the unpredictability of traffic changes. This may be caused by various elements such as rapid changes to traffic flow due to the start of new services from middle B operators with the previously mentioned business model changes; diversification of traffic characteristics due to the spread of numerous services, especially IoT (Internet of Things) services; temporary increases in demand due to large-scale events; and rapid responses to major disasters and cyber-attacks. For the unpredictable traffic changes above, network resource optimal control technology makes it possible to respond to temporary changes in demand, and cyber-attack suppression control technology can achieve stable service quality during a cyber-attack. These two kinds of technology are used as network configuration algorithms within the network abstraction technologies, and are capable of handling unpredictable traffic changes. 3. Network abstraction technologiesWith network abstraction technologies, the network copes with business model changes using two network technologies. One offers combinations of various network elements, and the other automatically controls networks based on middle B operator requirements (Fig. 2).
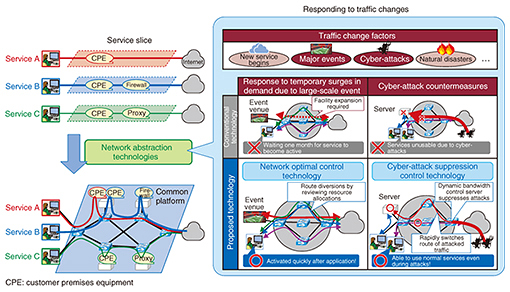
3.1 Technology offering combinations of various network elementsWith these technologies, we can define virtual networks that combine network elements for middle B operators as service slices and enable abstraction and customization of service slices according to middle B operators’ use cases. Service slices support patterns in which network functions and the physical configuration are concealed and middle B operators entrust the specific configuration to us, as well as patterns in which middle B operators specify the physical configuration themselves. An example of the former would be holding a videoconference for a maximum of 10 bases within an end-to-end delay of not more than 500 ms, where the specific physical configuration is entrusted to us. An example of the latter could be placing a videoconferencing control server in a Tokyo datacenter, with the physical configuration specified. With the entrusting pattern based on middle B operator requirements, the deployment and inter-functional path of the required network and application functions are automatically determined according to the resource usage situation and service requirements. As a result, even operators (such as those from other industries participating in the Hikari Collaboration Model) who could not previously develop network-using services due to a lack of detailed knowledge about the network can now easily initiate services. With the specified physical configuration pattern, we can support some middle B operators such as existing carriers and Internet service providers (ISPs) who require the maintenance and operation model where they understand the network’s specific physical configuration and can request to change the configuration as needed according to service usage conditions. We have succeeded in providing services responding to the needs of diverse middle B operators by supporting both of these patterns. 3.2 Technology to automatically control networks based on middle B operator requirementsThis technology can automate at a stroke the processes from the determination of the network configuration through to the configuration of physical equipment based on middle B operators’ requirements. With this technology, automated processing takes place with a series of virtual network function installations and equipment settings based on catalogues (service slice templates whose contents were previously determined) selected by middle B operators to match the service requirements. Prompt, easy service provision is achieved by providing functions for automating a series of network configuration processes to middle B operators as service slices. In this way, by combining the two network abstraction technologies described above, network-using middle B operators can simply and promptly provide more diverse services than were previously available. 4. Network resource optimal control technologyWith virtualized networks such as NetroSphere, we provide services by assigning physical network resources to service slices created based on middle B operator requirements [2]. These resource allocations enable free and flexible operation, but the allocation has an impact on facility use efficiency, service quality, and reliability. We aim to control resources appropriately in response to various traffic changes, so here, we introduce network optimal control technologies applied to respond to temporary increases in demand (Fig. 3).
When hosting new services with physical networks that already accommodate numerous services, capacity may be lacking due to insufficient usable resources, and new services may not be accommodated. In such cases, we can accommodate the relevant service capacity by reviewing the overall network resource allocation. For example, we can assume there will be large-scale demand for fixed periods such as during the Olympics and the World Cup. With conventional technology, problems with insufficient resources can be solved by expanding the facilities in advance. For the carrier, however, the equipment remains idle after the event is over and becomes a case of over-investment. Moreover, customers have to wait for the service to launch during the period of facility expansion, so the application must be completed long before the actual usage period. Accordingly, network resource optimal control technology does not involve expanding the facilities but instead accommodates new demand by redeploying existing services to alternative routes. This technology uses features of virtual networks capable of flexibly changing service slices and physical resource mapping. In this case, however, numerous restrictions must be considered. From the standpoint of operational costs, it is preferable to limit the number of resource-redeployed services as much as possible. From a service quality standpoint, it is necessary to preserve quality conditions required at different levels for each service, including bandwidth, delay, and packet loss ratios. Moreover, from a facility cost standpoint, it is desirable to expand surplus resources as much as possible after resource redeployment. The number of combinations of services for which resource redeployment is possible and that enable alternative routes is huge. Thus, it is very difficult to calculate the optimal solution to meet the above-mentioned restrictions from among all combinations. However, solutions can be discovered quickly using heuristic solutions*1. With this network resource optimal control technology, it is possible for carriers to effectively exploit existing facilities and for customers to use services promptly.
5. Cyber-attack suppression control technologyWe have been conducting research on cyber-attack suppression control technology in order to prevent cyber-attacks such as harmful distributed denial of service (DDoS) attacks*2 (Fig. 3). DDoS attacks not only impede services supplied from targeted servers but also have an impact (e.g., congestion) on the network path links that cyber-attack traffic flows through. This becomes a problem for both middle B operators and carriers. Furthermore, with conventional means to prevent cyber-attacks that install security products on networks, it is necessary to forward all cyber-attack traffic to the security products. At such times, the security products may not function very well due to issues such as the previously mentioned route congestion. Accordingly, in addition to security products, cyber-attack suppression control technology limits the impact of cyber-attacks by controlling whole network paths and bandwidths. Examples of specific techniques include diversion route high-speed recalculation to accelerate route switching by searching for local diversion routes in the event of network congestion caused by DDoS attacks. This is deemed applicable for large networks such as ISP networks. Another technique is dynamic bandwidth control to limit the impact of cyber-attacks by dynamically controlling bandwidth so that the volume of traffic flowing to the target is distributed evenly at multiple gateways at the network endpoint nodes, and service is maintained. By using these technologies, we can provide customers with stable service quality even during cyber-attacks.
6. Future developmentAny of the three technologies introduced in this article can be considered important factors in the need to realize robust networks that can respond to changes in the NetroSphere concept. In the future, in order to accelerate the implementation of these technologies, we will undertake wide-ranging collaborations both in Japan and abroad with vendors and research institutes, open source groups, and others specializing in various fields and will push forward with establishing technologies through joint research development and verification tests. References
|
|||||||||||