|
|||||||||
|
|
|||||||||
|
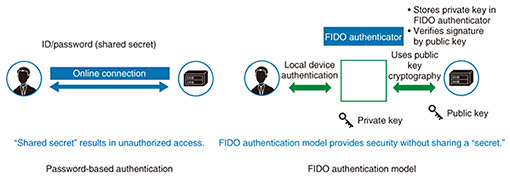
Feature Articles: Network Technology for Digital Society of the Future—Research and Development of Competitive Network Infrastructure Technologies Vol. 17, No. 6, pp. 37–40, June 2019. https://doi.org/10.53829/ntr201906fa11 Privilege Sharing and Transfer Based on Passwordless AuthenticationAbstractResearch is underway at the NTT laboratories on an authentication platform that provides both security and convenience. This article describes secure and passwordless authentication platform technology for application to a variety of services that use smartphones and other mobile devices that have grown in popularity. This technology is expected to be applied to a wide array of services to improve their convenience of use. Keywords: authentication, passwordless, FIDO 1. IntroductionThe explosive increase in the use of mobile devices such as smartphones has been accompanied by the ability to use all sorts of online services regardless of location. Although the method of authentication using an identifier (ID) and password has become commonplace when using individual services, it requires the user to remember and input a different password for each service. This presents a problem in terms of convenience. There is also concern about spoofing (impersonation) due to leaked IDs and passwords. In response to these problems, we have been studying technologies with the aim of achieving secure and convenient authentication. 2. FIDO-related technologyThe FIDO (Fast IDentity Online) Alliance proposes an authentication method using public key encryption technology to achieve secure and convenient authentication (Fig. 1) [1]. One set of FIDO specifications presents the Universal Authentication Framework (UAF) protocol that assumes the use of mobile devices such as smartphones. The UAF protocol stores a private key for authentication in a secure area of the mobile device (such as a secure element (SE) or trusted execution environment (TEE)) and uses the mobile device as an authentication token. Using public key encryption technology at the time of authentication provides a high level of security without the need for secret information (such as a password) shared by the server and device. Passwordless authentication can also be achieved using some means of personal confirmation such as biometric authentication that mobile devices are beginning to provide as standard.
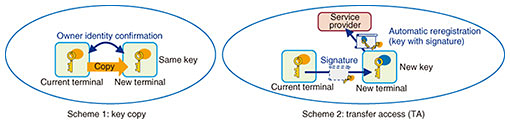
3. Overview of convenience-enhancing technologyVarious service providers have begun to introduce FIDO-certified authentication ecosystems reflecting the ongoing spread of FIDO technology. We at the NTT laboratories seek to make people’s lives more convenient by enabling users to share privileges to use products and services provided by the application with FIDO technology. When using public key encryption technology that is used in secure authentication methods such as FIDO UAF, as many keys as the number of services being used will be registered in the mobile device, but when using a new device such as when upgrading to a new model, a user has to re-register those keys. The proposed convenience-enhancing technology would ease the burden of such re-registration by providing a mechanism for securely and easily sharing keys among multiple devices. An overview of key-sharing (transfer) schemes at the core of this convenience-enhancing technology is shown in Fig. 2. Scheme 1 is a key-copy scheme that duplicates a private key stored in the SE/TEE area of a device in a new device. To ensure security, this scheme incorporates various methods to verify the user of a device such as biometric authentication and identity confirmation using a digital certificate, and it uses proximity communication methods to eliminate communications over the Internet such as near-field communication or Bluetooth [2]. In addition, key sharing between two devices can be achieved by a simple device operation using biometric authentication and device-pairing via device-to-device contact.
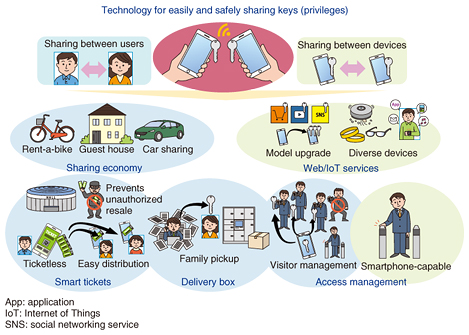
Scheme 2 is a transfer access (TA) [3] scheme developed by researchers at the University of Washington in Seattle, USA. In this scheme, a new device notifies the server (service provider) that the user of a new device is the same as a user whose private key has already been registered by sending a digital signature calculated using the private key. This scheme is effective when a service provider needs to detect the addition of a device by a user, though it requires the modification of an authentication server. 4. Application of convenience-enhancing technologyWe are researching methods to achieve privilege sharing (transfer) to use services and resources by using mechanisms such as those for sharing private keys among devices used in convenience-enhancing technology [4]. Enabling the current device and a new one in the TA scheme in Fig. 2 to correspond to user A and user B, respectively, public key registration by user B will mean, from the viewpoint of the service provider, that user A who already has the privilege to use a service has passed it to user B. This technology can be applied not only to sharing privileges to use services between devices but also to various types of services by using it to grant certain privileges from one user to another (Fig. 3).
5. Future outlookWe described a secure and convenient method for sharing and transferring privileges to use services without the need for passwords. Looking to the future, we plan to study specific systems for applying this method to a variety of services as shown in Fig. 3 to achieve a general-purpose and sophisticated authentication platform and add value to related services. References
Trademark notesAll brand names, product names, and company/organization names that appear in this article are trademarks or registered trademarks of their respective owners. |
|||||||||