|
|||||||||||||||||
|
|
|||||||||||||||||
|
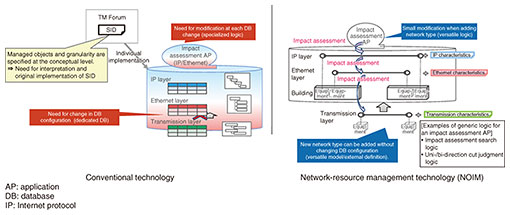
Feature Articles: Access Network Technologies for IOWN Vol. 20, No. 9, pp. 34–39, Sept. 2022. https://doi.org/10.53829/ntr202209fa4 Technical Approaches for Operations to Accelerate Digital TransformationAbstractNTT Access Network Service Systems Laboratories is undertaking research and development into operations technology to enable smart operations and explore new business areas through such operations. We believe that collaborative business operations involving multiple players will be both deeper and more common in the future. Therefore, we are focusing on the promotion and expansion of digital transformation involving multiple players. This article introduces our recent efforts in self-evolving zero-touch operations technology and business design support technology based on operation-process classification. Keywords: digital transformation, network operation, business design 1. Characteristics, trends, and desired directions of access network operationsAccess networks are widespread across Japan. Since they directly interface with service users and maintenance staff at indoor and outdoor telecommunications facilities, access operations are deeply linked with these various players’ and users’ businesses. There have been growing expectations for digital transformation (DX) across various infrastructure companies to address social issues, such as the shrinking working-age population [1] and aging infrastructure [2]. Demand for new services, such as private fifth-generation mobile communication (5G)/6G and mobility as a service (MaaS) using automated driving, is expected to grow. Triggered by measures taken against infectious diseases, lifestyles and work styles have become increasingly diversified. These trends will increase our sharing and mutual use of facilities and services with players other than telecommunications carriers, as well as collaboration in their operations. Thus, it is important to develop a mechanism that breaks through business boundaries and enhances productivity. In view of the above, the Access Network Operation Project at NTT Access Network Service Systems Laboratories is developing smart operations that accompany the progress of the Innovative Optical and Wireless Network (IOWN). Specifically, we are aiming to actualize an ecosystem in which various players can easily collaborate with each other using their respective business operations, systems, and data, and cause a chain reaction of value creation (DX acceleration) within this ecosystem. The form of collaboration can vary depending on the business structure of each player. The targets for collaboration can also differ, ranging from information to systems and organizations. We are conducting research and development (R&D) into operations technologies from these various perspectives and working with NTT Group companies to prepare for their commercial introduction. This article introduces our latest efforts to enable collaborative end-to-end operations across multiple network layers and domains. Specifically, it introduces self-evolving zero-touch operations technology, which features versatile network-information management with autonomous analysis and decision on the basis of this management, and business design support technology based on operation-process classification, which improves work efficiency by enabling business-support and business-execution organizations in the field to develop a common understanding. 2. Self-evolving zero-touch operations technologyNTT Access Network Service Systems Laboratories is undertaking R&D into making network operations dramatically smarter. We believe that one of the keys to self-evolving smart operations is end-to-end operations coordination that manages network resources across multiple domains and carriers. We are developing technologies for end-to-end operations coordination from the following perspectives: (1) Network-information management for handling end-to-end resources across multiple layers and domains; (2) Analysis and decision for the provision of network services on the basis of the network information made available in (1). Figure 1 shows the network-information management referred to in perspective (1). A network-information database is traditionally built for each service provider, for each service, and for each network type. This hinders operations and maintenance across multiple network layers and poses a barrier to enabling operations coordination. A solution to these problems is a generic versatile network-information model. For example, TM Forum has standardized one such model as the Shared Information and Data Model (SID) [3]. However, since the SID specifies managed objects and granularity only at the requirement or conceptual level, service providers need to interpret the SID in accordance with the type of networks they manage and develop their own implementations. Since the time and cost service providers can expend in developing their implementations are usually restricted, it is difficult for them to take generality and future extensibility into account when studying the details of the data model. Thus, their implementations tend to be specific to the network type to be added at the time. The result is that each time a new network type to be managed is added, it is necessary to change both the network-information database and logic.
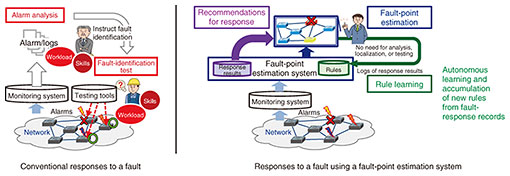
NTT Access Network Service Systems Laboratories has developed the Network Operation Injected Model (NOIM), which is now in commercial use [4]. NOIM is a technology for handling network information using a versatile unified model. NOIM does not stop at the conceptual level but specifies a versatile, extensible, network-type independent mechanism, which reduces both the need for modifying databases and logic and the cost that is incurred each time a new network type is to be added. NOIM makes it easy to specify a versatile model that focuses on network-type independent properties, such as point and connectivity, specified in the SID. It uses a mechanism by which network-type dependent attributes and inter-layer relationships can be defined and held externally, thus ensuring high extensibility. As a result, even if network types change or new network types emerge, there is no need to change the databases, and the changes needed in processing logic are also greatly reduced. Network information from multiple domains can also be handled uniformly at the data-format level, enabling interoperability, and making it easy for service providers and services to make mutual use of each other’s network information and rules. The analysis and decision referred to in perspective (2) are regularly applied to various tasks for the provision of network services such as facility planning, responses to service orders, and fault monitoring and handling. Such analysis and decision is highly dependent on operators’ skills and imposes a considerable workload. To solve this problem and enable optimal analysis and decision—which is not possible with human operators—there have been initiatives in the field of network operations to use network-artificial intelligence (AI) such as autonomous network and AI operations (AI Ops). The R&D efforts of NTT Access Network Service Systems Laboratories are aimed at further expanding the positive effects of network-AI by combining optimal analysis and decision made possible by network-AI with the versatility, extensibility, and interoperability provided by NOIM. The following technologies for fault-point estimation and fault response are introduced as examples of our efforts. When a network failure occurs, it is necessary to identify its fault point from a large amount of event information that has complex causal relationships across multiple layers and select response actions appropriate to the cause of the fault. Such identification and selection are heavily dependent on the skills of the operators and impose a considerable workload. To solve these problems, NTT Access Network Service Systems Laboratories has developed a technology that automates fault-point estimation and response-action selection. The technology is now in commercial use [5]. Figure 2 illustrates the process of network fault-point estimation and response-action selection. In this technology, a network-AI learns the relationships (rules) between fault information and fault points across multiple network layers from alarms, analysis, and identification results related to previously occurring faults. When a network failure occurs subsequently, the network-AI estimates the fault point on the basis of these learned rules. It also recommends a method for minimizing the recovery time or recovery actions on the basis of the actions taken in the past for each type of cause of fault.
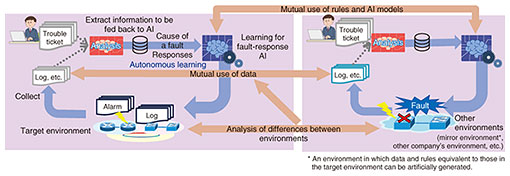
The network-AI requires a large amount of past data to learn how to identify faults and deal with them. Therefore, the network-AI cannot adequately respond in cases where it was only introduced recently and the volume of accumulated data is still small, or where a particular type of event occurs so rarely that the network-AI is not likely to be able to learn about it from the accumulated data. The training stage of the network-AI currently requires the skills and work of experts for the preparation of appropriate training data. A solution to these problems is to use data generated in actual network operations as training data. Therefore, NTT Access Network Service Systems Laboratories is developing an autonomous learning technology that automatically extracts the causes of faults and response actions from logs and trouble tickets that have been created in actual network operations and feeds them back into the network-AI. We are also aiming to enable training data, rules, and AI models that are generated in a network environment or derived from each network-AI applied to the environment to be used in other environments. For this purpose, we are developing an inter-environment transfer technology, which analyzes the differences between different network environments using the interoperability of NOIM, and converts training data, rules, and AI models for application in other environments [6]. Figure 3 illustrates the transfer of data, rules, and AI models between different environments.
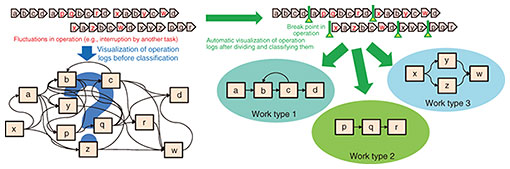
3. Business design support technology based on operation-process classificationBusiness reforms had been led by business-support organizations. Based on its bird’s-eye view of a company’s business operations and the insights it had gained from business trends, a business-support organization makes reform proposals that it thought had high potential for creating substantial improvements in productivity. However, such reforms sometimes lost touch with actual business conditions and required much time and cost to implement. Due to the spread of robotics process automation (RPA) and low-code/no-code automation, DX has been led by business-execution organizations. Such an organization implements its reform proposals that are based on detailed perspectives and insights closely related to actual business operations. While such reforms are highly compatible with business reality and bring about immediate effects, there are growing concerns about only achieving the individualized optimization from this approach. We believe that, if we are to further enhance the effectiveness of DX in the coming years, it is important to ensure paraconsistency between the above two approaches on the basis of a common understanding between business-support and business-execution organizations. This common understanding should be founded in turn on a shared perception of how the actual business is run (business reality). The operations of a business-execution organization (actual operations) vary depending on the differences or changes in the business environment, such as business needs and trends relating to other companies. Consequently, there is a gap between actual operations and either designed operations, which provide the basis for the formulation of standard operational flows and operations manuals, or assumed operations, which are derived from the observation of a selective sample of operations and interviews with business-execution staff. This gap makes it difficult to develop a common understanding of the reality of actual operations. At NTT Access Network Service Systems Laboratories, we are developing a technology intended to deepen common understanding between business-support and business-execution organizations by enabling accurate and easy understanding of actual operations on the basis of objective data. Since the success of business reform is highly dependent on an accurate understanding of actual operations, we developed a business design support technology that is based on operation-process classification. It focuses on actual operations on terminals, which are among the operational tasks that a business-support organization has difficulty in understanding accurately [7]. This technology offers a comprehensive mechanism for obtaining operation logs, which provide powerful objective data about operations on terminals and, on the basis of them, for visualizing, editing operational flows, and generating an operation automation scenario for RPA. The technology provides the following features, which are keys to understanding the gap between designed/assumed operations and the actual situation. (1) Classification of operation logs into work types When operations are designed or assumed, the process of service order reception, for example, is broken down into several work types, such as order-information registration and operational-task reservation, and it is assumed that several service orders are handled one by one and these work types are executed sequentially. However, in actual operations, it is not uncommon that different work types for several service orders are executed in parallel. Individual operation logs are also obtained without differentiation by operation type. Therefore, it is difficult to identify the gap between designed/assumed operations and the actual situation simply by arranging operation logs in chronological order. Our technology automatically detects the points in a series of operation logs where the operation type changes and visualizes the operation logs after dividing and classifying them. This makes it possible to understand actual operations by operation type [8]. Figure 4 shows the classification of operation logs into work types.
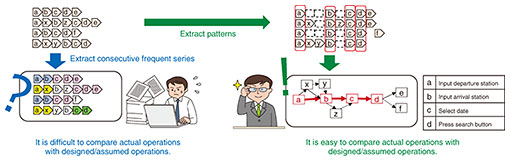
(2) Extraction of frequent operation patterns Among the operations that occur in the course of work, designed/assumed operations only cover typical operations, such as entering a value in an input field or pressing a button. In contrast, fully logged operations are more comprehensive and include those operations that are normally ignored in designing or assuming operations but are necessary to the process of entering a value in an input field such as making keystrokes to change selections in a list box or scrolling a screen. This means that there are various operations that are not included in designed/assumed operations, and these vary depending on the task being performed at the time. Even if a series of consecutive operations that occur frequently are extracted from the operation logs, it is not possible to compare them with the operation patterns that occur frequently in designed/assumed operations. Our technology is used to examine not only the consecutive operations in the operation logs but also the relationships between distant operations in the logs and automatically extract the most frequently occurring relationships, enabling actual operations to be compared with frequently occurring operation patterns in design/assumed operations. Figure 5 shows the extraction of frequently occurring operation patterns.
To enable the design of highly productive and feasible operations and prompt incorporation of these into actual operations that can be implemented continuously, we will refine and expand the technologies mentioned above to promote and deepen common understanding and develop a mechanism that facilitates the use of not only RPA but also various information and communication technologies in business operations. 4. OutlookWe are aiming to develop a mechanism that makes it possible to increase productivity across diverse players and explore new business areas through collaboration of these players in a manner that takes advantage of their respective assets. For this purpose, we will develop technologies that facilitate collaboration among players and achieve self-evolution of analysis and decision. Through this R&D, we will strive to deepen collaboration with our partners and produce results in a timely manner. References
|
|||||||||||||||||