|
|||||||
|
|
|||||||
|
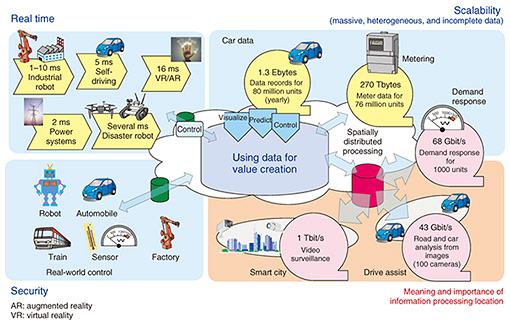
Feature Articles: NTT Tsukuba Forum 2017 Workshop Lectures Vol. 16, No. 4, pp. 23–28, Apr. 2018. https://doi.org/10.53829/ntr201804fa3  Internet of Things Approach for Creating Value in Various FieldsAbstractThe Internet of Things (IoT) is expected to create high value services in various fields. We believe that the era in which IoT is fully utilized will have requirements different from those of the past for information and telecommunications networks. In this article, the influence of the new IoT era on networks and information processing is described, along with the resulting requirements. The NTT laboratories’ efforts and assumed usage scenarios are also introduced. These Feature Articles are based on lectures given during workshops at the Tsukuba Forum 2017 held in October 2017. Keywords: sensing, data exchange, prediction of social activities 1. Requirements for information communication and role of technology in the Internet of Things (IoT) eraIn line with the increasing use of personal computers and the Internet and the adoption of mobile phones, information communication has become an essential function for social activities and daily life, and its value has rapidly increased and changed with society. From the era in which simple connections were highly valued, as typified by telephones for the purpose of communication between people, access to the Internet in recent years has become valued for the acquisition of information and knowledge. The number of connections from devices, or things, to the network already exceeds the number of people connected using terminals, so the era of IoT has already begun, where communication between things and people, as well as between things and things is the main focus. Currently, IoT, which integrates cyberspace and real-world society, is mainly utilized for linking things, gathering data, and visualizing social events and the movement of goods. In the future, it will also be used for utilizing the collected data. We believe that with progress, we will be able to predict what will happen at social events, and to control events to make social and industrial activities safer and more efficient. As this kind of utilization becomes more and more common, IoT technology will advance to the point where cyberspace will rapidly process and analyze the collected data, feed the results back to the real world, and/or control the real world. One ultimate goal of information communication is autonomous driving, which is expected to become a service highly valued in society. Current IoT devices are vertically integrated, and few IoT devices are connected in certain fields, for example, agriculture and smart cities. However, work on horizontal linking is accelerating in the fields of manufacturing, automobiles, and transportation. This trend is expected to create new value services in a wide range of business fields. We believe that different requirements and much larger scale-out will be required to realize the high potential of IoT. The requirements placed on information communication to fully achieve an IoT society are shown in Fig. 1, along with the amount of time and/or amount of data for each function.
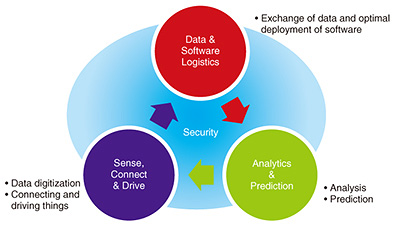
The first requirement is security. In becoming part of society, IoT can be expected to trigger greater damage from cyber-attacks than those triggered by communication between people, so stronger than ever security measures are needed. The second requirement is real-time response. In order to control a machine, information processing and communication must offer more real-time performance. For functions such as machine control in factories, safe driving assistance for automobiles, and the use of augmented reality and virtual reality, the response times of information communication and information processing must be on the order of milliseconds. The third requirement is scalability. For example, the total amount of probe data of cars, the images recorded by cars, and the data from smart meters will be on the order of petabytes. Moreover, the collected data are expected to be heterogeneous, as they will be generated by quite different objects. Accordingly, scalable information processing that can handle extremely large amounts of heterogeneous and incomplete data is required. The fourth requirement is value creation. We cannot realize sufficient value simply by gathering large sets of diverse data. To achieve efficiency in production and social activities, we must be able to utilize and analyze the collected data and create new value that can be used for forecasting and control. In addition to these four requirements, it is necessary to meet specific IoT usage requirements. In many of the usage scenarios expected for IoT, the consumption of data and information will exhibit strong regionality. For example, data will be gathered at intersections for automatic driving support, while data will be gathered from devices such as meters and sensors for the purpose of energy conservation. In this way, the IoT will exhibit data locality; thus, an information communication and information processing architecture that can cope with this feature will be required. In addition, certain IoT requirements cannot be solved by technology alone, for example, protection of rights to utilize the collected data safely and appropriately, and the necessity of forming a social agreement on the scope of use of such data. In response to these requirements, the NTT laboratories have formulated a basic functional architecture that can realize a complete IoT system. We are utilizing some of the current technologies available in the market, while also working on the research and development (R&D) of key technology groups [1]. These technology groups—classified into four roles—will realize the full-fledged IoT system. These roles are indicated in Fig. 2. The first role is Sense, Connect & Drive. This involves digitizing information on goods, responding to diversity, and securing storage capacity and the necessary user interfaces to exchange information with cyberspace via the network. The second role is Data & Software Logistics. This brings the collected data to the best location for use and/or processing and in doing so satisfies the real-time and information scalability requirements (Fig. 1), which are key IoT requirements. In addition, this includes the deployment of software/algorithms to use/process the data at the appropriate location. The third role is Analytics & Prediction, which combines big-data analysis technology such as the rapidly expanding machine learning and artificial intelligence (AI) technology, to provide new value services such as data analytics visualization and prediction. Security is the fourth role, and the functions necessary for each phase and process are used in conjunction with the other three roles. The IoT system will be achieved by integrating these four roles.
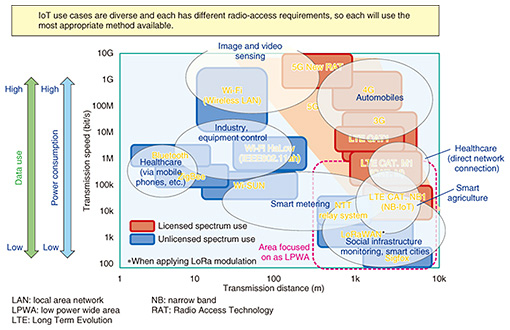
2. Technology group that realizes IoT and an application exampleIn this section, some of the main IoT services expected to be introduced in the future are described. 2.1 Biometric sensingOne expected IoT service involves the collection and processing of biological data as represented by healthcare. In collaboration with Toray Industries, Inc., the NTT Group has developed the functional material called “hitoe” that enables biometric sensing simply by having a user wear clothes made of the material. Work is underway on enhancing sensing performance and utilizing it in unprecedented environments and actions. For example, car drivers wearing “hitoe” shirts will have their biological data detected in real time, enabling early detection of driving problems such as driver fatigue. Moreover, by linking the shirt to a control system, we can contribute to the improvement of public safety as well as the improvements in company efficiency such as knowing when to change drivers of buses or other vehicles. 2.2 Wireless accessVarious wireless access protocols currently exist for IoT, and it seems that changes in the existing methods and the development of new methods will continue into the future. A typical IoT radio access method is shown in Fig. 3, with the communication distance on the horizontal axis and the communication speed on the vertical axis.
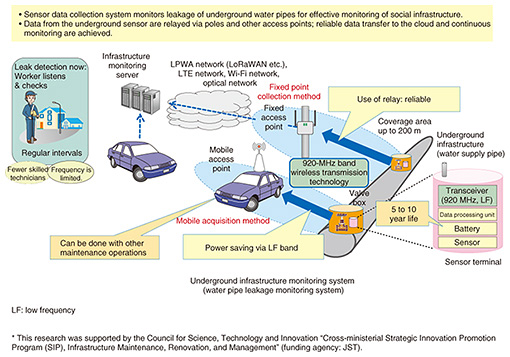
With the growing social expectations for IoT, the wireless access technology called LPWA (low power wide area) is attracting attention since it offers wide area coverage and can be used for long periods due to its low power consumption; these benefits outweigh its low speeds. We note that in IoT, infrastructure monitoring, which requires long-term and wide-range data acquisition, is well supported by LPWA for smart cities. Another trend is the collection and processing of large amounts of video data. This demands high-capacity wireless access. NTT laboratories’ current efforts in using IoT to monitor the leakage from water supply pipes installed underground are shown in Fig. 4. Water leaks are currently found by conducting manual listening tests on site; this demands a high level of skill and the presence of an expert in the field. By collecting data in cyberspace on the sounds of water pipes, we believe that remote inspections will become possible using information technology such as machine learning. However, radio waves from devices attached to underground pipes will be strongly attenuated. Our solution is to acquire data reliably with a high level of power-saving by using radio relay systems on public utility poles. The high level of power efficiency achieved enables data collection for a long time after installing the sensor underground. With the cooperation of local governments, we are now proceeding with verification trials in the field for early social implementation.
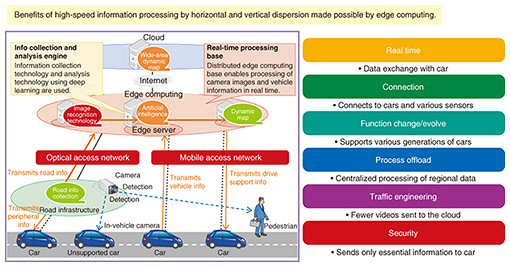
2.3 Edge computingIt is important for IoT to perform information processing in the most suitable location, and the technology to achieve this is edge computing. This technology sets a processing site, called the edge, between the cloud and the terminal and thus offers various information processing benefits by utilizing the spatial dispersion characteristics not provided by the cloud. For example, we can achieve the benefits of proximity and high responsiveness. Moreover, spatial dispersion allows us to offload terminal functions to the network. The NTT laboratories are also engaged in the R&D of this technology, not only in our own labs, but also with partners to realize attractive usage scenarios and projects [2]. An application example of this technology in automatic driving support is shown in Fig. 5. We believe edge computing will be used for horizontally distributed processing by providing information on the next intersection as well as vertically distributed processing for providing various pieces of map information. This will lead to the realization of automatic driving support; mass data will be gathered and recognized, and the circumstances that can be expected to change from moment to moment will be predicted and passed to the moving car.
2.4 Data utilizationThe IoT is expected to utilize diverse heterogeneous data and create new value services. It is important to make good use of open data created by public agencies and local governments, especially for realizing smart cities. At the NTT laboratories, we are working with partners to improve the efficiency of urban management by combining open data with local data and by conducting modeling and data analysis utilizing AI technology [3]. From now on, we will pursue technical verification in real fields, while aiming to continue horizontal studies to solve the various problems hindering the realization of smart cities. 2.5 SecurityThe devices used in IoT are diverse, and since there are many devices that do not follow the Internet protocol, security must be provided using a different approach. The NTT laboratories are working on the R&D of anomaly detection technology. This can detect security risks from the behaviors of networks and devices. With this approach, security is assured by processing information observed from outside the device, so additions and changes to devices with limited processing capability and existing facilities are relatively easy. This is particularly important in factories where various protocols are used. 3. ConclusionThe NTT Group is using the B2B2X (business-to-business-to-X) model to solve social problems through collaboration with various partners in a wide range of fields. This approach will ensure the technical development of IoT. The aim is to create new business value by incorporating the knowledge and know-how from different industries. AcknowledgmentPart of this work (water pipe leak monitoring) was supported by the Council for Science, Technology and Innovation “Cross-ministerial Strategic Innovation Promotion Program (SIP), Infrastructure Maintenance, Renovation, and Management” (funding agency: JST). References
■Author profileShuichi YoshinoExecutive Research Engineer, Senior Manager, Wireless Systems Innovation Laboratory, NTT Network Innovation Laboratories. He received a B.E. and M.E. in mechanical engineering from Kanazawa University in 1990 and 1992. He joined NTT in 1992 and worked on the development of a satellite Internet system and wireless networking technologies. He has contributed to the practical application of active radio frequency identification devices for logistics and wireless access technologies for gas meter reading systems. He is currently engaged in R&D of wireless technology for IoT and mobile access. |
|||||||