 |
|||||||||||||||||||||||||||||||||||||||||||||
|
|
|||||||||||||||||||||||||||||||||||||||||||||
Vol. 6, No. 1, pp. 11–17, Jan. 2008. https://doi.org/10.53829/ntr200801sp1 New Paradigm for Practical Cryptosystems without Random OraclesAbstractThis paper introduces a new paradigm for making various types of cryptographic primitives such as authenticated key exchange and key encapsulation without random oracles under three assumptions: the decisional Diffie-Hellman assumption, target collision resistant hash functions, and a class of pseudo-random functions. It describes a new two-pass authenticated key exchange (AKE) protocol (based on the public key infrastructure model) that is comparable in efficiency to the most efficient of the existing protocols and secure (under these assumptions), whereas existing efficient two-pass AKE protocols are secure in the random oracle model. This protocol is shown to be secure in the (currently) strongest security definition, the extended Canetti-Krawczyk (eCK) security definition. This paper also describes a key encapsulation mechanism (KEM) that is secure against adaptive chosen ciphertext attacks (i.e., CCA-secure) under these assumptions and almost as efficient as the Kurosawa-Desmedt KEM. The schemes presented this paper are validity-check-free, which implies that combining them with validity-check-free symmetric encryption (data encryption mechanism) will yield validity-check-free (e.g., free of message authentication code) CCA-secure hybrid encryption.
1. IntroductionThe concept of public-key cryptosystems was introduced by Diffie and Hellman in 1976 to solve the key agreement problem over insecure networks (like the Internet). The standard security notion of a public-key cryptosystem (encryption) is security against adaptive chosen ciphertext attacks (i.e., CCA-security), and there are two major methodologies for designing practical CCA-secure public-key encryption: one is based on the random oracle model and the other on the standard model. A CCA-secure scheme in the standard model provides a real security guarantee, whereas a CCA-secure scheme in the random oracle model is guaranteed to be secure under unrealistic idealization of a hash function as an ideal random function. One of the most important topics for the last ten years has been to design a truly practical public-key cryptosystems in the standard model*1. The most common paradigm for designing practical public-key cryptosystems that are secure in the standard model is to combine a trapdoor function (e.g., Diffie-Hellman or RSA (Rivest, Shamir, Adleman) function) and target collision resistance (TCR) hash functions, where the security is proven under a trapdoor function assumption (e.g., DDH (decisional Diffie-Hellman) or strong RSA assumption) and the TCR hash function assumption [3]–[5]. This paper introduces a new paradigm for designing practical public-key cryptosystems, where a class of pseudo-random functions (PRFs) PRFs with pairwise-independent random sources (πPRFs), is used in addition to a trapdoor function (Diffie-Hellman function) and TCR hash function. The concept of a PRF was introduced by Goldreich, Goldwasser, and Micali [6]. The PRF has been shown to exist if and only if a one-way function exists [6], [7]. Therefore, the existence of a PRF is one of the weakest assumptions, so it is one of the most fundamental primitives in cryptography*2. Since a TCR hash function (and the slightly more general concept of the universal one-way hash function) has also been shown to exist if and only if a one-way function exists [9], [10], the TCR hash function and PRF are on the same level as (the most) fundamental primitives in cryptography. In practice, a well-designed efficient hash function can be assumed to be a TCR hash function, and such a hash function with a random seed as part of the input (or a keyed hash function) can be assumed to be a PRF (and a πPRF). Authenticated key exchange (AKE) protocols have been extensively studied to enhance the security of the Diffie-Hellman (DH) key exchange protocol, which was proposed in 1976, because the DH protocol is not secure against the man-in-the-middle attack[11]–[17]. This paper presents a two-pass AKE protocol that has the following properties.
This paper also presents a CCA-secure (i.e., secure against adaptive chosen ciphertext attacks) key encapsulation mechanism (KEM) under these assumptions that is almost as efficient as the Kurosawa-Desmedt KEM [5]. The schemes presented in this paper are validity-check-free, which implies validity-check-free (e.g., free of message authentication code (MAC-free)) CCA-secure hybrid encryption if they are combined with validity-check-free CCA-secure symmetric encryption (data encryption mechanism (DEM)). Therefore, their ciphertexts can be decrypted with no validity-check.
2. Preliminaries2.1 Notation
A function f : If A is a probabilistic machine or algorithm, A(x) denotes the random variable of A's output on input x. Then, yR← A(x) denotes that y is randomly selected from A(x) according to its distribution. If a is a value, A(x) → a denotes the event that A outputs a on input x. If A is a set, y U← A denotes that y is uniformly selected from A. If A is a value, y ← A denotes that y is set to A. In this paper, the underlying machines are considered to be uniform Turing machines, but the results can easily be extended to non-uniform Turing machines. 2.2 Decisional Diffie-Hellman (DDH) assumptionLet k be a security parameter and For all k∈
Let A be a probabilistic polynomial-time machine. For all k ∈, AdvDDHA(k) ← | Pr [A(1k, ρ)→1| ρ U← The DDH assumption for { 2.3 Pseudo-random Function (PRF)Let k∈ – A family of random seeds {Seekk}k∈ – A family of PRFs indexed by k,Σ R← Seedk, σ U← Σ, D R← Domk, and R R← Rngk, where each such function Fkσ,Σ,D,R maps an element of D to an element of R. There must exist a deterministic polynomial-time algorithm that on input 1k,σ, and ρ, outputs Fkσ,Σ,D,R (ρ). Let AO be a probabilistic polynomial-time machine with oracle access to O. For all k, we define AdvPRFF, A(k) ←|Pr [AF(1k,D,R )→1] − Pr[ARF(1k,D,R ) → 1]|, where Σ R← Seedk, σ U← Σ, D R← Domk, R R← Rngk, F ←Fkσ,Σ,D,R, and RF : D → R is a truly random function (¢Ïρ∈D RF(ρ) U←R). F is a PRF family if, for any probabilistic polynomial-time adversary A, AdvPRFF, A(k) is negligible in k. 2.4 Pseudo-random function with pairwise-independent random sources (πPRF)Here, we introduce a specific class of PRFs, πPRFs. Let k∈ We then define a πPRF family for F. Let Σ R← Seedk, D R← Domk, R R← Rngk, and RF: D → R be a truly random function (¢Ïρ∈DRF(ρ) U← R). Let IΣ be a set of indices regarding Σ such that there exists a deterministic polynomial-time algorithm, fΣ: IΣ → Σ, that on input i ∈IΣ, outputs σi ∈Σ . Let σi0, σi1, ..., σit(k) be random variables indexed by IΣ, where ij ∈IΣ (j = 0, 1, ..., t(k)) and t(k) is a polynomial of k. Let σi0 be pairwisely independent from other variables, σi1, ..., σit(k) and each variable be uniformly distributed over Σ. That is, for any pair of (σi0, σij) (j = 1, ..., t(k)), for any (x, y)∈Σ2, Pr[σi0→ x ∧σij → y] = Pr[σi0 → x ] • Pr[σij → y] = 1/|Σ|2. Let AF, IΣ be a probabilistic polynomial-time machine A that queries qj ∈D along with ij ∈IΣ to F and receives the reply F kσij,Σ,D,R (qj) for each j = 0, 1, ..., t(k). Let ARF, IΣ be the same as AF, IΣ except that Fkσijk, Σ D, R, (q0) is replaced by RF(q0). For all k, we define AdvπPRFF, IΣ, A(k) ← |Pr[AF, IΣ(1k,D ,R ) → 1] − Pr[ARF, IΣ(1k,D ,R ) → 1]|. F is a πPRF family with index {(IΣ, fΣ)}Σ∈Seedk, k∈ 2.5 Target collision resistant (TCR) hash functionLet k∈ – A family of key spaces indexed by k. Each such key space is a probability space of bit strings denoted by KHk. There must exist a probabilistic polynomial-time algorithm whose output distribution on input 1k is equal to KHk. – A family of hash functions indexed by k, h R← KHk, D R← Domk, and R R← Rngk, where each such function Hhk,D,R maps an element of D to an element of R. There must exist a deterministic polynomial-time algorithm that on input 1k, h, and ρ, outputs Hhk,D,R (ρ). Let A be a probabilistic polynomial-time machine. For all k, we define AdvTCR H, A(k)← Pr [ρ∈D ∧ρ≠ρ* ∧Hhk,D,R (ρ) =Hhk,D,R (ρ*)ρ| R← A(1k, ρ*, h, D, R)], where D R← Domk, R R← Rngk, ρ* U← D and h R← KHk. H is a TCR hash function family if for any probabilistic polynomial-time adversary A, AdvTCR H, A(k) is negligible in k. 2.6 PKI-based authenticated key exchange (AKE) and eCK security definitionThis section outlines the eCK security definition [16] for two-pass AKE protocols based on the public key infrastructure (PKI) model and follows the description in [17]. The eCK definition assumes that there are n parties, which are modeled as probabilistic polynomial-time Turing machines. We assume that these parties have agreed some common parameters (common reference strings) in the AKE protocol before the protocol is started. The parameter selection mechanism is out of the scope of the AKE protocol and the (eCK) security model. Each party has a static public-private key pair together with a certificate that binds the public key to that party. ˆA (or ˆB ) denotes the static public key A (or B) of party A(B) together with a certificate. The certifying authority (CA) is not assumed to require parties to prove possession of their static private keys, but the CA is required to verify that the static public key of a party belongs to the domain of public keys. Here, two parties exchange static public keys A, B and ephemeral public keys X, Y; the session key is obtained by combining A, B, X, Y and possibly session identities. A party A can be activated to execute an instance of the protocol called a session. Activation is made via an incoming message that has one of the following forms: ( ˆA, ˆB) or ˆB, ˆA, X). If A was activated with ( ˆA, ˆB), then A is called the session initiator; otherwise, it is called the session responder. Session initiator A creates ephemeral public-private key pair (X, x) and sends ( ˆB, ˆA, X) to session responder B. B then creates ephemeral public-private key pair (Y, y) and sends ( ˆA, ˆB, X, Y) to A. The session of initiator A with responder B is identified via session identifier ( ˆA, ˆB, X, Y), where A and B are said to be the owner and peer of the session, respectively. The session of responder B with initiator A is identified as ( ˆB, ˆA, Y, X), where B is the owner and A is the peer. Session ( ˆB, ˆA, Y, X) is said to be a matching session of ( ˆA, ˆB, X, Y). We say that a session is completed if its owner computes a session key. The adversary M is modeled as a probabilistic polynomial-time Turing machine and controls all communications. Parties submit outgoing messages to the adversary, who makes decisions about their delivery. The adversary presents parties with incoming messages via Send(message), thereby controlling the activation of sessions. In order to capture private information that may leak, adversary M is allowed the following queries: – EphemeralKeyReveal(sid) The adversary obtains the ephemeral private key associated with session sid. – SessionKeyReveal(sid) The adversary obtains the session key for session sid, provided that the session has a session key. – StaticKeyReveal(pid) The adversary learns the static private key of party pid. – EstabllishPatry(pid) This query makes it possible for the adversary to register a static public key on behalf of a party. In this way, the adversary completely controls that party. If a party pid is established by EstabllishPatry(pid) query issued by adversary M, then we call the party dishonest. If a party is not dishonest, we call it honest. The aim of adversary M is to distinguish a session key from a random key. Formally, the adversary is allowed to make a special query Test(sid*), where sid* is called the target session. The adversary is then given with equal probability either the session key K*, held by sid*, or a random key R* U← {0, 1}|K*|. The adversary wins the game if he correctly guesses whether the key is random or not. To define the game, we need the notion of a fresh session as follows: Definition 1. (fresh session) Let sid be the session identifier of a completed session owned by an honest party A with peer B, who is also honest. Let —sid be the session identifier of the matching session of sid, if it exists. We define session sid to be fresh if none of the following conditions hold: –M issues a SessionKeyReveal(sid) query or a SessionKeyReveal(—sid) query (if —sid exists), – —sid exists and M makes either of the following queries: both StaticKeyReveal(A) and EphemeralKeyReveal(sid) or both StaticKeyReveal(B) and EphemeralKeyReveal(—sid), – —sid does not exist and M makes either of the following queries: both StaticKeyReveal(A) and EphemeralKeyReveal(sid) or StaticKeyReveal(B). Now we are ready to present the eCK security notion. Definition 2. (eCK security) Let K* be the session key of the target session sid* that should be fresh, R* U← {0, 1}|K*|, and b* U← {0, 1}. As a reply to Test(sid*) query by M, K* is given to M if b* = 0; R*; otherwise, R* is given. Finally, M outputs b ∈{0, 1}. We define A key exchange protocol is secure if the following conditions hold: – If two honest parties complete matching sessions, then they both compute the same session key (or both output an indication of protocol failure). – For any probabilistic polynomial-time adversary M, AdvAKEM(k) is negligible in k. This security definition is stronger than the original form of Canetti-Krawczyk security [11] and it simultaneously captures all the known desirable security properties for authenticated key exchange including resistance to key-compromise impersonation attacks, weak perfect forward secrecy, and resilience to the leakage of ephemeral private keys. 2.7 Key encapsulation mechanism (KEM)A KEM scheme is the triplet of algorithms, Σ= (K, E, D), where 1. K, the key generation algorithm, is a probabilistic polynomial-time algorithm that takes a security parameter k∈ 2. E, the key encryption algorithm, is a probabilistic polynomial-time algorithm that takes as input public key pk and outputs a key/ciphertext pair (K*, C*). 3. D, the decryption algorithm, is a deterministic polynomial time algorithm that takes as input secret key sk and ciphertext C* and outputs key K* or ⊥ (⊥ means that the ciphertext is invalid). For all (pk, sk) output by key generation algorithm K and for all (K*, C*) output by key encryption algorithm E(pk), D(sk, C*) = K* holds. Here, the length of the key |K*| is specified by l (k), where k is the security parameter. Let A be an adversary. The attack game is defined in terms of an interactive computation between adversary A and its challenger C. The challenger C responds to the oracle queries made by A. The attack game (IND-CCA2 game) used to define security against adaptive chosen ciphertext attacks (IND-CCA2) is described below. 1. The challenger C generates a pair of keys (pk, sk) R← K(1k) and gives pk to adversary A. 2. Repeat the following procedure q1(k) times, for i = 1, . . . , q1(k), where q1(•) is a polynomial. A submits string Ci to a decryption oracle, DO (in C), and DO returns Dsk (Ci) to A. 3. A submits the encryption query to C. The encryption oracle EO in C selects b* U← {0, 1} and computes (C*, K*) ← E(pk) and returns (C*, K*) to A if b* = 0 and (C*, K*) if b* = 1, where R* U←{0, 1}|K*| (C* is called the target ciphertext). 4. Repeat the following procedure q2(k) times, for j = q1(k)+1, . . . , q1(k) + q2(k), where q2(•) is a polynomial. A submits string Cj to a decryption oracle, DO (in C), subject only to the restriction that a submitted text Cj is not identical to C*. DO returns Dsk (Cj) to A. 5. A outputs b ∈{0, 1}. We define the IND-CCA2 advantage of A, AdvKEMAIND-CCA2(k) ← |Pr[b = b*] − 1/2| in the above attack game. We say that a KEM scheme is IND-CCA2-secure (secure against adaptive chosen ciphertext attacks) if, for any probabilistic polynomial-time adversaryA, AdvKEMAIND-CCA2(k) is negligible in k. 3. New AKE protocol
3.1 ProtocolLet k∈ ( Party A's static private key is (a1, a2, a3, a4) U← ( Similarly, Party B's static private key is (b0, b1, b2, b3, b4) U← ( A and B set πPRF and PRFs F ← Fk,ΣF,DF,RF, ˜F ← ˜Fk, Σ˜F, D˜F, R˜F and ˆF ← ˆFk,Σ ˆF,DˆF,RˆF, where ΣF← To establish a session key with party B, party A performs the following procedure. 1. Select an ephemeral private key (˜x1, ˜x2) U← {0, 1}k × {0, 1}k. 2. Compute ˜a ←Σ4i=0 ai mod p (x, x3) ← ˆF˜x1 (1k) + ˜F˜a (˜x2) mod p (as two-dimensional vectors) and the ephemeral public key (X1 ← Gx1, X2 ← Gx2, X3 ← G1x3). Note that the value of (x, x3) (and ˜a) is only computed in a computation process of the ephemeral public key from ephemeral and static private keys. 3. Erase (x, x3) and the whole computation history of the ephemeral public key. 4. Send ( ˆB, ˆA, X1, X2, X3) to B. Upon receiving ( ˆB, ˆA, X1, X2, X3), party B verifies that (X1, X2, X3) ∈ 1. Select an ephemeral private key (˜y1, ˜y2) U←{0, 1}k × {0, 1}k. 2. Compute ˜b ← Σ4i=0 bi mod p (y, y3) ← ˆF˜y1 (1k) + ˜F˜b (˜y2) mod p (as two-dimensional vectors) and the ephemeral public key (Y1 ← Gy1, Y2 ← Gy2, Y3 ← G1y3) 3. Erase (y, y3) and the whole computation history of the ephemeral public key. 4. Send ( ˆA, ˆB, X1, X2, X3, Y1, Y2, Y3) to A. Upon receiving( ˆA, ˆB, X1, X2, X3, Y1, Y2, Y3), party A checks if he sent ( ˆB, ˆA,X1, X2, X3) to B. If so, A verifies that (Y1, Y2, Y3) ∈ To compute the session key, A computes σA ← Y1a1+ca3Y2a2+ca4Y3x3B1xB2dx , and B computes σB ← X1b1+db3 X2b2+db4X3y3A1yA2cy , where c ← HA( ˆA, ˆB,Y1, Y2, Y3) and d ← HB( ˆB, ˆA, X1, X2, X3). If they are correctly computed, then σ← σA (=σB). The session key is K ← Fσ (sid), where sid ← ( ˆA, ˆB, X1, X2, X3, Y1, Y2, Y3). 3.2 SecurityTheorem 1. 4. New KEM scheme4.1 SchemeThis section shows a CCA-secure KEM scheme. Let k∈ Secret key: The secret key is sk←(x1, x2, y1, y2) U← Public key: G1 U← The public key is pk ← ( Encryption: Choose r U← (C1, C2) is a ciphertext and K is the secret key to be shared. Decryption: Given (z, w, C1, C2), check whether (z, w, C1, C2)∈ If it holds, compute K ← Fσ (pk, C1, C2). 4.2 CCA securityTheorem 2.The new KEM scheme is IND-CCA2-secure if the DDH assumption holds for { 5. Concluding remarksThis paper introduced a new paradigm for making various types of cryptographic primitives such as authenticated key exchange and key encapsulation without random oracles under the three standard assumptions: the DDH assumption, TCR hash functions, and πPRFs. These schemes are secure without random oracles and almost as efficient as the most efficient schemes secure in the random oracle model. Therefore, they are good candidates for replacing practical schemes in the random oracle model and will have many practical applications*3 [18]. References
|
|||||||||||||||||||||||||||||||||||||||||||||








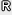

 , f
, f