|
|||||||||||||||||||||||||
|
|
|||||||||||||||||||||||||
|
Global Standardization Activities Vol. 7, No. 1, pp. 29–33, Jan. 2009. https://doi.org/10.53829/ntr200901gls Recent Standardization and Other Activities in Ubiquitous Open Platform ForumAbstractThis article describes standardization activities related to technical specifications in the Ubiquitous Open Platform Forum (UOPF), past progress, and the future outlook. UOPF has established outcomes, such as technical specifications and reference guides, and it released all of them to the public in April 2007. Trials and experimental proofs have been done using these established specifications.
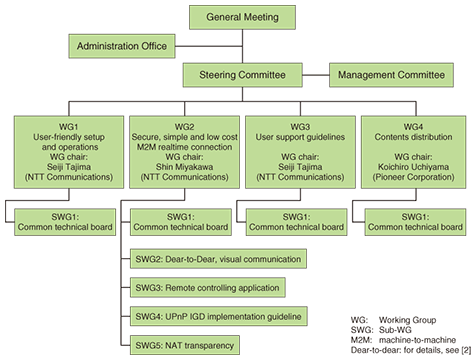
1. UOPFThe Ubiquitous Open Platform Forum (UOPF) [1] is a technical forum established by fourteen electric appliance manufacturers and Internet service providers (ISPs) in February 2004. The members have worked to promote Internet-accessible home electric/electronic appliances, as well as to widen the broadband market by standardizing network specifications. The purpose of UOPF is to establish an open common platform that will facilitate easy setup of electronic devices, safe online billing, and realtime data communications among home electronic devices. The UOPF member companies will also work closely with application and content providers in order to create common frameworks. UOPF has four Working Groups (WGs). Their directives are shown in Fig. 1.
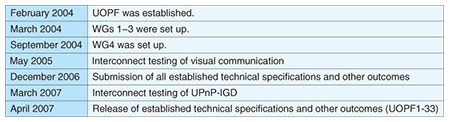
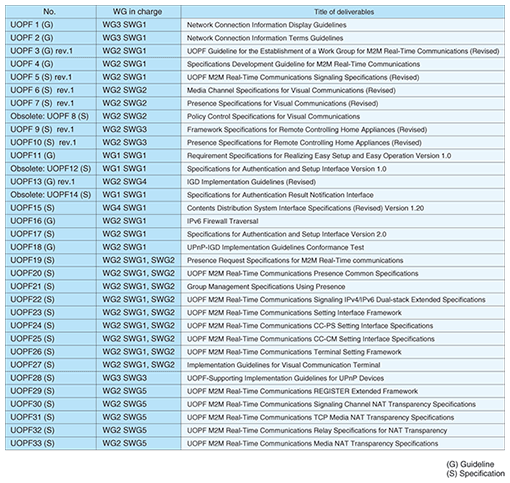
2. Standardization in UOPFThe progress of standardization of technical specifications in UOPF is given in Table 1. UOPF released established outcomes in April 2007; these are listed in Table 2. The standardization policy is based on open specifications made by other standardization bodies such as the Internet Engineering Task Force (IETF), Digital Living Network Alliance (DLNA), and Public Key Cryptography Standards (PKCS). The main open specifications used in UOPF are:
After the initial release of standards, new goals were established at the last UOPF general meeting (April 19, 2007), as listed below.
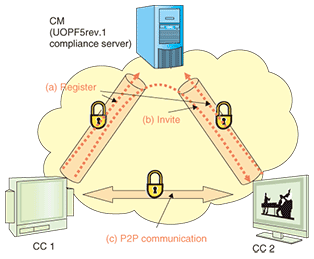
3. Usage trends of UOPF specificationsOne example of a technical test using UOPF specifications is the “Universal Plug and Play (UPnP) interconnectivity test”, which was a theme of the “next generation home network demonstration test” [3] of the Ministry of Internal Affairs and Communications in March 2008. In that test, we evaluated the behavior of a variety of SOHO (small office home office) routers as UPnP Internet gateway devices (UPnP-IGDs), using UOPF18-compliance testing tools. Meanwhile, NTT Communications is providing a free connectivity trial of a UOPF5rev.1-compliant server on the Internet [4]. The purpose of the trial is to promote the development of new applications and services. It is particularly aimed at m2m-x (machine-to-machine for anything) communication [5]. 4. Standardization policy of UOPF WG2This section explains the established policies of UOPF WG2. Its standardization policies focus on security, simplicity, and low cost. People using home appliances are usually not familiar with the latest network technology, so security and simplicity are important policies for UOPF WG2 discussions. Established specifications suggest the enhancement of security and simplicity by providing functions for authentication, encryption, easy setup, etc, which are provided from the UOPF WG2 compliance server. Because the client/server (C/S) communication model is more expensive because it requires servers to be set up, UOPF WG2 used a peer-to-peer (P2P) communication model that makes media connections between two devices without a relay server. This resulted in a large reduction in relay server cost. 5. Basic mechanism in UOPF WG2This section explains the basic mechanism of UOPF5rev.1 (Fig. 2) which was established as a main technical specification of UOPF WG2. In UOPF5rev.1, a general “SIP server” is called the “Communication Manager (CM)”, and a “User Agent (UA)” is called the “Communication Client (CC)”.
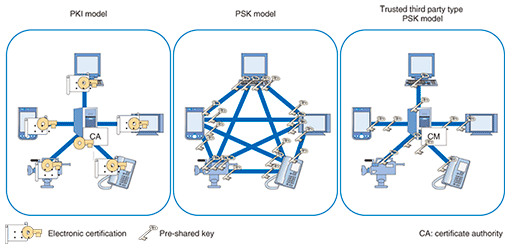
First, the CC on the network registers its identification (ID) on CM in advance, using a SIP REGISTER message, as shown by (a) in Fig. 2. In this registration sequence, an encrypted communication channel is established between the CM and CC using IPsec or TLS. In the CM registration procedure, a registered user is authenticated using a pre-shared key (PSK) or electronic certification. Second, when starting the actual end-to-end communication, the CC starts the session by designating its ID of the other CC in an INVITE message, as shown by (b). This INVITE message is transmitted to the CM. Through the exchange of these INVITE messages, CCs share various kinds of information such as IP addresses, ports, and key data for encryption, and they then reach agreement on the protocol to be used for end-to-end connections. After that, end-to-end direct communication will be available without the CM. This is called P2P communication, as shown by (c). It is difficult to enhance this mechanism’s scalability when the PSK model is used because the model expects CCs to manage many keys that are used to connect the other individual CCs. In the public key infrastructure (PKI), the CC only has to manage one key, so it is easier to obtain scalability than in PSK. However, certification management is complicated for ordinary users, so the ease of use may be lower. Hence, UOPF WG2 recommends the use of a trusted third party (TTP) type PSK model, in which each CC manages only one key for communicating with CM, with the CCs trusting the CM (Fig. 3).
6. Future outlookThe technology has been developed through trials and discussions about the specifications among various manufacturers and ISPs, making this technology ready for commercialization. New applications besides those for home electronic appliances have been developed. Some parts of the UOPF outcomes have been proposed to the Broadband Forum and to IETF in order to promote those technologies. From now on, we will try to create a new market by strengthening partnerships and accelerating service development. References
|
|||||||||||||||||||||||||