|
|||||||||||||
|
|
|||||||||||||
|
Special Feature: Trend of Network Security Technologies Vol. 8, No. 7, pp. 5–10, July 2010. https://doi.org/10.53829/ntr201007sf2 Traffic Monitoring and Analysis TechnologiesAbstractThis article introduces trends in the development of technologies for monitoring and analyzing anomalous traffic in a multifaceted manner by utilizing traffic-flow information to solve the problem of attacks on the network.
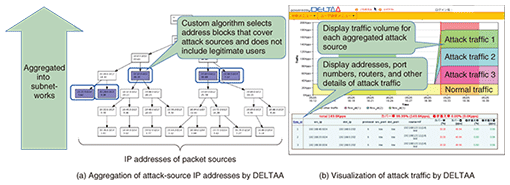
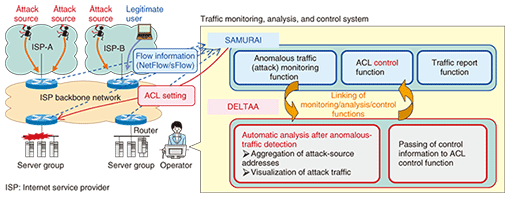
1. IntroductionWith attacks on the Internet becoming increasingly diverse, the development of countermeasures is an important issue. Distributed denial of service (DDoS) attacks have been known to bring down servers by flooding them with a huge volume of invalid packets. Other examples include the cache poisoning attack, which tampers with the content of a domain name system (DNS) by providing it with a bogus IP address pointing to a phishing site, and the route hijacking attack, which disables access to a server by supplying bogus routing information. NTT Information Sharing Platform Laboratories is researching and developing network security technologies for monitoring and analyzing traffic in a multifaceted manner to defend against such a diversified array of attacks. In this article, we introduce technologies for countermeasures to DDoS attacks, DNS attacks, and unexpected border gateway protocol (BGP) route changes and describe trends in the development of flow quality monitoring technologies. 2. Technologies to counter DDoS attacksThe SAMURAI [1] traffic analysis system is an example of NTT Group technology for defending against DDoS attacks. It uses sampled flow information to analyze specific attack patterns using a signature function and to analyze anomalous increases in traffic using a baseline detection function. These analyses enable the source of an attack on specific servers to be identified and attack traffic to be filtered through the use of a router’s access control list (ACL) or a Cisco Guard DDoS mitigation appliance. This technology has been put to actual use by NTT Communications. In some cases, however, there are many DDoS attack sources, which makes it difficult to set an ACL with the IP addresses of the packet-sending sources. In such a situation, the DELTAA [2] anomalous traffic identification system can be used. The DELTAA system recognizes hosts with sharp increases in traffic as attack sources and aggregates them into subnetworks. This process involves precise calculations to avoid including legitimate users (Fig. 1(a)). In this way, a very large number of attack sources can be identified in terms of a small number of subnetworks, enabling attack traffic to be easily filtered by a router’s ACL. This system is also equipped with functions for visualizing the attack traffic volume for each aggregated attack source, attack start time, etc. (Fig. 1(b)). These functions enable an operator to understand the nature of a DDoS attack clearly and quickly.
Our aim at present is to implement DELTAA in a form that links up with SAMURAI (Fig. 2).
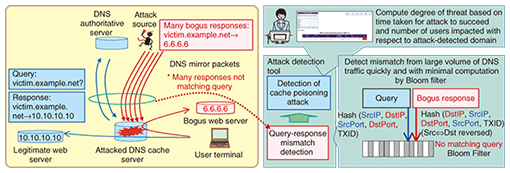
3. Technology to counter DNS attacksOne type of DNS attack is the DNS cache poisoning attack, which inserts a DNS record pointing to a phishing site. Such an attack can be detected using the KOROKU DNS-attack monitoring and analysis tool, which monitors and analyzes flow information [3] exhaustively sampled from the traffic addressed to a certain DNS server. In the case of a DNS cache poisoning attack, a large number of name-resolution response packets that do not match any queries arrive at the targeted DNS server. Such an attack can therefore be detected by monitoring and exhaustively analyzing sampled flow information (Fig. 3). The KOROKU tool is currently undergoing prototype testing and demonstrations using actual equipment.
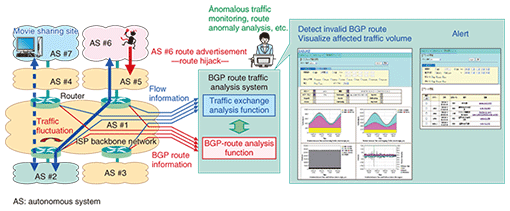
4. Technology to counter unexpected BGP route changesUnexpected or invalid BGP route changes, such as BGP-route-hijacking or misconfiguration, suddenly lead to traffic diversions. Moreover, they might lead to traffic disruption or congestion on other backbone links. The SASUKE BGP route traffic analysis system is used to detect traffic changes caused by unexpected BGP route changes. It collects BGP route information by direct BGP peering with BGP routers and detects unexpected or invalid BGP route changes and route fluctuations that affect traffic by monitoring for and analyzing any correlations among the flow information collected from different routers. Since the number of BGP routes in the Internet is huge, testing each and every route for legitimacy is unrealistic. For this reason, when SASUKE detects fluctuations in BGP routes, it focuses on traffic changes for the top rank-N traffic volume and then analyzes the correlation between a traffic change and the BGP route change involved. When a traffic change caused by an invalid or unexpected route change occurs, SASUKE issues an alert and prompts the operator to investigate the cause of the route fluctuation (Fig. 4).
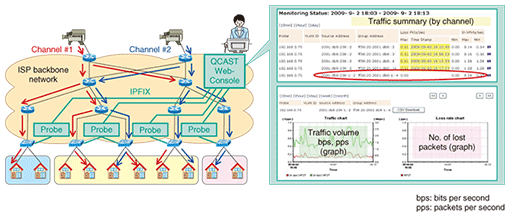
The SASUKE system is currently undergoing prototype testing and demonstrations in the field with an eye toward implementation in a form that links up with DELTAA and SAMURAI. 5. QoS monitoring technologiesWith the spread of realtime applications such as IPTV (Internet protocol television) and VoIP (voice over Internet protocol), it has become increasingly difficult to troubleshoot failure points between the network and users. The monitoring of transmission quality has consequently become an important issue. The QCAST IPTV (multicast) QoS (quality of service) monitoring tool, which consists of Probe and Web-Console, monitors the transmission quality on the network side. To monitor IPTV transmission quality, QCAST Probe measures packet loss and packet inter-arrival time fluctuations by keeping track of the sequence number of RTP (Real-time Transport Protocol) headers. To achieve efficient measurement for multiple IPTV multicast channels on the network side, QCAST Probe uses filtering and systematic time-based sampling defined in PSAMP [3], which is suitable for keeping track of the RTP header sequence number. Accordingly, QCAST Web-Console collects this data via the IPFIX protocol [4] and then visualizes its own data. Visualization and investigation for IPTV channels on Web-Console let the operator easily check whether IPTV streams are being transmitted at an appropriate level of quality (Fig. 5).
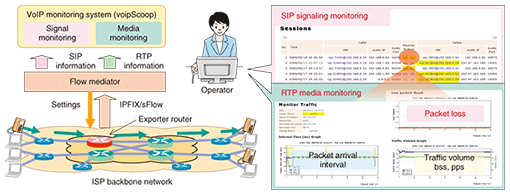
There is also the voipScoop VoIP QoS monitoring tool, which monitors and analyzes VoIP transmission quality by a similar technique. voipScoop achieves signal-media-linked monitoring by first monitoring SIP (session initiation protocol) signaling information to identify the associated RTP media information and then monitoring the transmission quality of that RTP medium (Fig. 6).
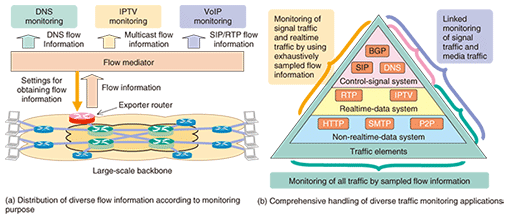
At present, QCAST and voipScoop are undergoing prototype testing and demonstrations with actual equipment with an eye toward future implementation. 6. Multipurpose traffic monitoring technologySince it is important for flow information to be used in various forms to cope with increasingly diverse network monitoring applications, we are researching and developing a traffic data mediation tool called ScoopFlow. The core element of this technology is flow-based, or packet-based, traffic data mediation. This tool collects various types of traffic data from routers and distributes it to appropriate collectors (monitoring/analysis equipment). If necessary, it also controls routers that can collect the required flow- or packet-based data (Fig. 7(a)).
Finally, ScoopFlow deals comprehensively with diverse monitoring applications from three viewpoints: (1) monitoring all traffic by sampled flow information, (2) monitoring packet-based traffic data by focusing on specific traffic flows with ACL-based filtering, and (3) performing linked monitoring of signal and media traffic (Fig. 7(b)). This traffic data mediation technology should be deployed extensively in the network, and to that end, we are engaged in not only prototyping but also standardization activities through the IPFIX Working Group in the Internet Engineering Task Force (IEFT) [5]. 7. ConclusionAlthough we can expect attacks to become increasingly diversified from here on, we aim to efficiently raise the comprehensiveness of defenses by appropriately selecting and deploying the countermeasure technologies described in this article. In future research, we plan to conduct more field trials and demonstrations toward the practical deployment of these technologies. AcknowledgmentThis study was partly supported by the Ministry of Internal Affairs and Communications of Japan. References
|
|||||||||||||