|
|||||||||||||||||
|
|
|||||||||||||||||
|
Feature Articles: Quantum Cryptography Vol. 9, No. 9, pp. 38–42, Sept. 2011. https://doi.org/10.53829/ntr201109fa8 Differential Phase Shift Quantum Key Distribution (DPS-QKD) ExperimentsAbstractNTT Basic Research Laboratories has been researching and developing differential phase shift quantum key distribution (DPS-QKD), a new QKD protocol. This article introduces the basics of this protocol, proof-of-principle experiments, the development of a prototype system, and a field experiment done at the Tokyo QKD Network demonstration in October 2010.
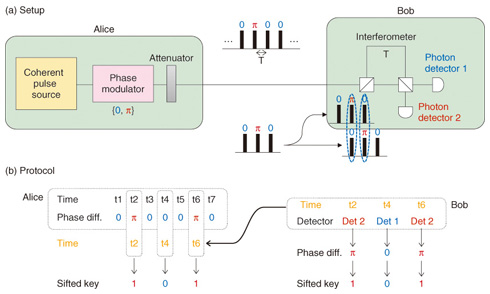
1. Differential phase shift quantum key distribution (DPS-QKD)Quantum key distribution (QKD), which is a cryptosystem that uses the principles of quantum mechanics, has recently been attracting much attention as a way to achieve ultimate security in communication. In 2003, NTT and Stanford University jointly proposed differential phase shift quantum key distribution (DPS-QKD) [1], which uses the fact that only part of the relative phase information of attenuated light pulses can be read out. The setup and protocol of DPS-QKD are shown in Fig. 1.
First of all, the sender (called Alice) prepares a coherent pulse train and modulates the relative phase of the light pulses randomly with 0 or p. The light is then sent to the receiver (Bob) after being attenuated such that the number of photons per pulse is less than 1. Bob uses a one-pulse delay interferometer to cause successive pulses to interfere and measures the relative phase information with a set of photon detectors located at the interferometer's outputs. Since the source photon power is weak, only part of the relative phase information can be read out, but the obtained relative phase should be exactly the same as the phase modulations at the sender. Bob records the timestamp when a photon was detected and which of the detectors clicked (relative phase information itself). He then generates a key by assigning bit 0 to relative phase 0 and bit 1 to relative phase p. Bob then sends back to Alice only the timestamp information. Alice uses this information and her phase encoding records to generate a key, which is called the sifted key*. Finally, after error-correction and privacy-amplification processes, final secure keys are generated and used in cryptic communication.
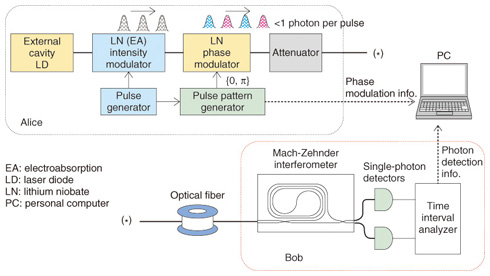
2. Proof-of-principle experimentsWe have demonstrated the principle of this protocol and evaluated the limits of the key distribution distances and key generation rates using real optical fibers. The experimental setup is shown in Fig. 2. Alice modulates the intensity of the light from a laser with a wavelength of 1551 nm to generate 1-GHz repetition pulses. Random phases 0 or p are encoded using a pulse pattern generator. After the light intensity has been adjusted to 0.2 photons per pulse on average, the pulses are sent into an optical fiber. Bob receives the light pulses from Alice and inputs them to a one-pulse delay interferometer and detects photons with the two single-photon detectors positioned at the interferometer's outputs. A time interval analyzer records the photon detection time and information about which of the detectors clicked. The sifted key is generated from this record by the abovementioned protocol, and the key generation rates and error rates are estimated.
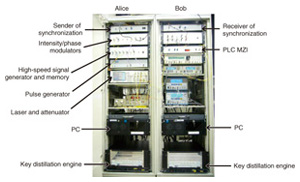
The main issues so far have been the stability of the interferometer and the performance of the photon detectors. To obtain stable photon interference, we used a Mach-Zehnder interferometer (MZI) based on planar lightwave circuit (PLC) technology using quartz glass waveguides; this technology was developed by NTT. Since the optical path difference was ten times longer than that of conventional optical communications, stabilization had previously been a problem, but this PLC MZI showed an extinction ratio of more than 20 dB (corresponding to a bit error of less than 1%), which enabled us to perform a successful demonstration. As for the photon detectors, performance improvement accompanies the use of a longer key distribution length. The first demonstration in 2004 used an InGaAs avalanche photodiode (APD), and 100-km distribution was demonstrated using a photon detector system by converting long-wavelength photons to a shorter wavelength and detecting them with a fast, high-efficiency Si photon detector [2]. In 2007, we succeeded in achieving 200-km distribution with superconductor-based single-photon detectors, which enabled us to raise the repetition frequency to 10 GHz [3]. As shown in Fig. 1, this protocol requires huge random numbers. While a pseudo-random generator is usually used, a fast physical random generator is necessary to improve the security. Recently, a random generator with a generation rate of more than 1 Gbit/s using chaotic fluctuations of laser light has been developed and applied to DPS-QKD experiments [4]. 3. Prototype systemDPS-QKD has been confirmed through several experiments, and we have started developing a prototype system. Its appearance is shown in Fig. 3. For the prototype implementation, we developed a high-speed signal generator and its memory unit using a field programmable gate array (FPGA). This is on Alice's side for generating signals to modulate the phase and for keeping them until the key generation stage. As in the proof-of-principle experiments, Alice modulates the intensity of the laser light to generate a 1-GHz pulse train and then modulates the relative phases depending on the phase signal from the FPGA board. After being attenuated, the pulses are sent to Bob. On Bob's side, the relative phases are detected with a PLC MZI and single-photon detectors, and the obtained signal is continuously retrieved by a time-interval analyzer and fed to a personal computer, where a sifted key is generated. At the same time, only the detection time is sent to Alice via a network. Alice extracts the phase information stored in the FPGA board according to Bob's detection times and generates a sifted key. Finally, the sifted keys on both sides are sent to the key distillation engine (developed by NEC), which executes error correction and privacy amplification and generates the final secret key for cryptic communication.
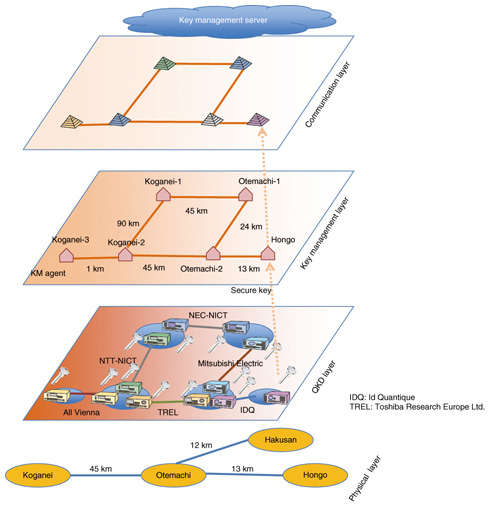
4. Field experimentsWith our prototype system, we participated in a testbed network experiment called Tokyo QKD Network [5], led by the National Institute of Information and Communications Technology (NICT). The participants were NEC, Mitsubishi Electric, NTT supported by NICT, Toshiba Research Europe, Id Quantique (Geneva), and the All Vienna team. This QKD network was constructed using the testbed optical fiber network JGN2plus, connecting nodes at Otemachi, Koganei, Hakusan, and Hongo. The network structure of this experiment is shown in Fig. 4. The transmission distances were Otemachi to Koganei: 45 km, Otemachi to Hakusan: 12 km, and Otemachi to Hongo: 13 km. There are many fibers in parallel on the Koganei-Otemachi, Otemachi-Hakusan, and Otemachi-Hongo routes and various network topologies are configured.
The lower layer, called the QKD layer, had six nodes; each team put its equipment at the nodes at both ends of a link. The QKD layer was constructed over the physical layer. For example, NTT used 90 km of fiber between Koganei and Otemachi in a loopback configuration, NEC used 45 km of fiber between Koganei and Otemachi, Mitsubishi used 24 km of fiber between Otemachi and Hakusan in a loopback configuration, and ID Quantique used 13 km fiber between Otemachi and Hongo. The secret key generated by QKD was supplied to the local key management agent and moved up to the key management layer. The key stored in the key management agent was used for cryptic communications such as a videoconference and voice communication. Between nodes that were not directly connected, the key was exchanged by being repeated at intermediate nodes. NTT, in collaboration with NICT, was in charge of the longest loop-back segment used in the experiment (about 90 km). With the combination of our prototype system and the superconducting single-photon detectors developed by NICT, we were able to achieve stable key distribution. The stability test of sifted key generation was successfully run for about 8 days, with average generation rate of 18 kbit/s and average bit error rate of 2.2%. The stability test of final key generation including error correction and privacy amplification ran stably for about 4 hours, with a generation rate of 2.1 kbit/s. At an international conference (Updating Quantum Cryptography and Communications, UQCC) [6] in Oct. 2011, this QKD network demonstrated live detection of eavesdropping and subsequent automatic changeover to the redundant standby route, enabling an ultimately secure videoconference. References
|
|||||||||||||||||