|
|||||||||
|
|
|||||||||
|
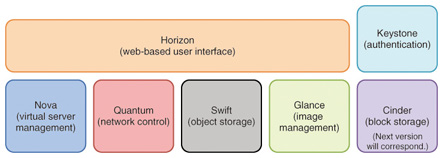
Feature Articles: Platform Technologies for Open Source Cloud Big Data Vol. 10, No. 12, pp. 6–12, Dec. 2012. https://doi.org/10.53829/ntr201212fa1 IaaS Platform Using OpenStack and OpenFlow Overlay TechnologyAbstractThis article describes how OpenStack and a virtual network controller that uses OpenFlow overlay technology can be orchestrated to deploy virtual environments with complex network configurations, as in on-premise systems, in an on-demand manner. 1. IntroductionThere is increasing use of infrastructure as a service (IaaS), in which virtual servers, virtual storage, and other such virtual environments are provided, as exemplified by Amazon Web Services. This situation has given rise to an open source software (OSS) community whose objectives are reduced cost and open development in the construction of IaaS platforms. 2. OpenStackOpenStack [1] is an OSS IaaS platform development project established by NASA and Rackspace in 2010. The NTT Group is among the 183 companies and 3386 individuals that currently make up that growing community. OpenStack version 5 was released in April 2012 under the code name “Essex”. OpenStack is one of the most prominent of the OSS IaaS platforms and is now being used in commercial services as well as for other purposes. In April 2012, 19 companies including AT&T, HP, IBM, Rackspace, and Red Hat established the OpenStack Foundation to promote the development and use of OpenStack, raising expectations for even more widespread adoption of the platform. OpenStack comprises multiple services (functional modules), including a virtual server management function, object storage, and network management. Users can select the services they need to flexibly construct an IaaS platform (Fig. 1). This article focuses on the platform’s virtual server management and network control functions. We describe a method of constructing a flexible virtual environment that combines virtual servers and virtual networks through cooperation with those OpenStack functions.
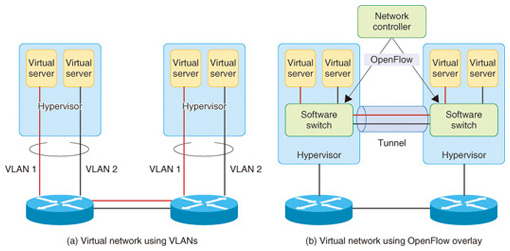
3. Virtual networksAs in hybrid clouds, there are use cases for cloud systems that include virtual networks as well as virtual servers to constitute virtual systems in a cloud environment while maintaining the system configuration and integrity with conventional enterprise systems. The virtual network is one kind of technology for implementing such use scenarios [2]. 4. Technology for implementing virtual networksA number of ways of connecting virtual servers to isolated customer virtual networks in the cloud have been proposed. One is to allocate a virtual local area network (VLAN) to each customer to form virtual networks in units of a VLAN. In the approach using VMware*1 or other such products, a particular VLAN is assigned to the virtual server. The virtual servers on the same VLAN engage in closed communication. This approach requires the prior setting up of a VLAN with switches and other communication devices in the datacenter. One method for connecting virtual servers that does not require control of the settings of communication devices is the overlay method, which involves extending tunnels between software switches on a hypervisor to establish communication paths between virtual servers running on the hypervisors. OpenFlow or other such tools are used to control the software switches (Fig. 2). Another method is the hop-by-hop method.
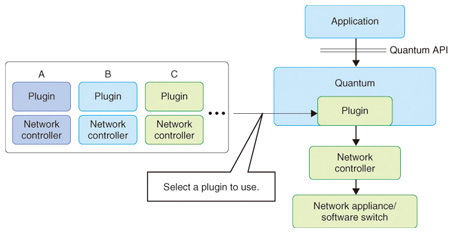
5. Network controllerIn OpenFlow, a server referred to as the network controller manages the creation, setup, and deletion of virtual networks. The network controller manages the network devices, software switches, and other functions on the hypervisor to construct virtual networks. Network controllers are provided by several companies (including NEC, Cisco, Nicira, and NTT), and each company has its own approach to network virtualization, including the methods described above. 6. OpenStack network control functionIn OpenStack, the network control function is provided by the Quantum service, which provides an application programming interface (API) for creating, setting up, and deleting virtual networks. One feature of Quantum is a plugin architecture. Quantum itself provides only common functions such as authentication and an API for higher-level applications. The virtual network functions are incorporated into the existing network controller. As described above, network controllers are already available from several third-party vendors, and flexible connection to the controllers is possible with Quantum plugins for the various controllers. That makes it possible to use any network function flexibly via a unified Quantum API (Fig. 3).
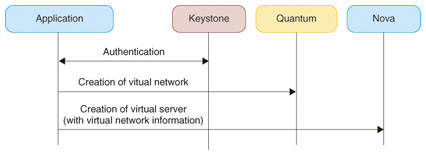
7. Cooperation between virtual server management and network control functionsIn OpenStack, management functions for virtual servers and networks are individual services that are called by their respective APIs to construct a virtual environment from virtual servers and virtual networks. A procedure for constructing a virtual environment from virtual servers and virtual networks is illustrated in Fig. 4. When OpenStack is used to provide an IaaS cloud service, these procedures for calling the various services are performed according to the use case and customer requirements to create the virtual environment.
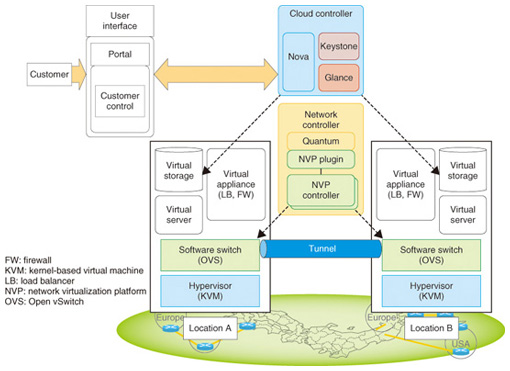
8. Work being done at NTTNTT is using OpenStack to construct an environment for verifying IaaS platforms in various use cases (Fig. 5). That environment uses a Nicira network controller as a network controller attached to a Quantum network controller to implement OpenFlow-based overlay virtual networks. Three typical use cases that were verified in our laboratory are described below.
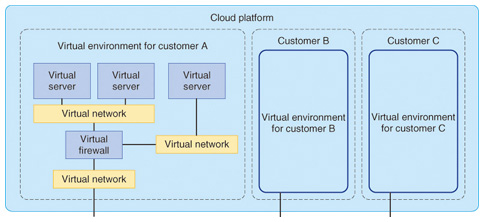
(1) Construction of a flexible virtual environment Any number of virtual networks can be created for a customer. Combining them with virtual servers enables the same configuration flexibility as provided by on-premises systems, including cascaded multilayer networks and demilitarized zones*2. Flexible system configuration enables effective use of existing software and other such assets as well as continuity in the use of firewalls and other network settings. It can therefore reduce the cost of system reconfiguration in the case of migration to a virtual environment. Because a virtual environment can be constructed in the cloud while maintaining compatibility with existing systems, the building of hybrid clouds that interwork with existing systems and cloud services can further expand the range of uses of cloud services. For this use case, a multilayer virtual network is constructed for each customer, and multiple virtual servers are placed on each network and assigned arbitrary IP (Internet protocol) addresses. We confirmed that communication with outside networks is possible in such a system (Fig. 6).
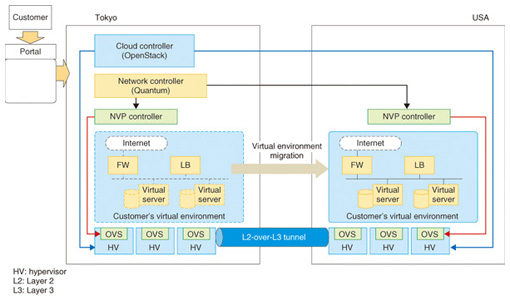
(2) Office migration Office migration is a use case that assumes the need to temporarily move a virtual environment to a different location to maintain business continuity during a disaster, pandemic, or other anomalous situation or to reduce the cost of electrical power. With the abovementioned overlay virtual network, a tunnel can even be constructed between remote software switches if IP connectivity is available. It is thus possible to construct a virtual network that involves a remote datacenter and create a single network environment that spans multiple locations. Doing so enables on-demand migration of virtual servers between datacenters without the need to change physical network settings. Previously, this would have required constructing individual Layer-2 VPNs and changing network settings within the datacenter. NTT has constructed an environment in which network controllers can be arranged to construct virtual networks between arbitrary datacenters and in which virtual servers can be freely placed and moved to enable unified control of multiple datacenters. We have confirmed that in this use case the customer can construct a virtual environment in any datacenter and move the entire environment to a different location as required (Fig. 7).
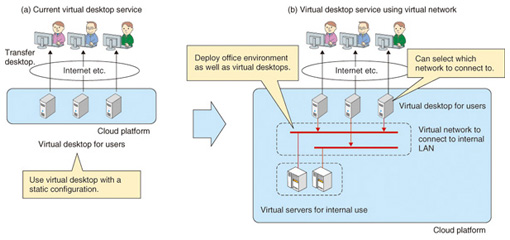
We demonstrated these results jointly with NTT Communications at the Open Networking Summit held in April 2012. The demonstration system was constructed at three actual locations in Japan, the USA, and Europe and migration of virtual environments among datacenters in different countries was verified. (3) Flexible virtual office environment In the flexible virtual office environment use case, an IaaS platform is applied as an in-house system to provide a virtual desktop environment to company employees. A virtual desktop is a service that provides remote access to the desktop of a virtual server, thus presenting the same working environment regardless of the terminal being used. Combining virtual network technology and a virtual desktop environment allows dynamic network construction and setup, making it possible to switch the virtual desktop to a different network without performing any extra configuration in the physical network. In this use case, the virtual-desktop users can switch networks on-demand according to their assigned tasks. We are now testing the basic operation of this use case and considering the application of OpenStack (Fig. 8).
9. Concluding remarksWe described the use of OpenStack, an OSS IaaS platform, in the construction of IaaS platforms. Specifically, we have verified use cases that involve interworking with a network controller and we presented examples of application to cloud services. For that task, we focused on the network, which is a core competence of the NTT Group. In the two years or so since the beginning of the OpenStack project, various proposals have been made by the active OpenStack community. We intend to continue to cooperate closely with that community to improve OpenStack functionality and raise the quality to the level required for commercial use. References
|
|||||||||