|
|||||||||||||||||
|
|
|||||||||||||||||
|
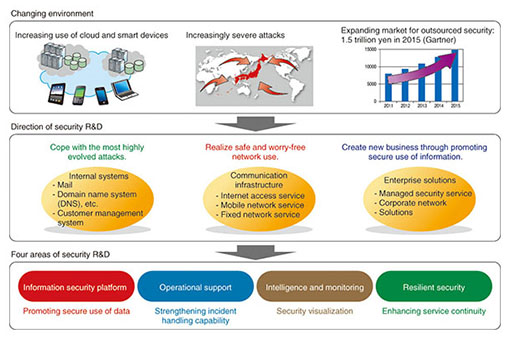
Feature Articles: Security Platform Technologies that Support Cloud Business Vol. 12, No. 7, pp. 1–4, July 2014. https://doi.org/10.53829/ntr201407fa1 Security R&D Activities for Cloud ServicesAbstractThe use of cloud services for handling economically and socially important information is increasing. In line with this trend, these services have become attractive targets for cyber attackers and have been exposed to more sophisticated cyber threats. Various efforts are underway at NTT to prevent these evolving cyber threats. In this article, we describe the activities of NTT Secure Platform Laboratories to provide safe and secure cloud services to our customers. Keywords: security, cloud, R&D plan 1. IntroductionCloud services, which provide storage and processing functions via the Internet, are becoming increasingly popular because of their economic advantages in reducing provisioning and operational costs as well as the convenience of being able to access them from various environments. As the use of smartphones to access the Internet has become more widespread, cloud services have accordingly provided more sophisticated and useful functions and have become an important infrastructure supporting our economy and society. The incorporation of cloud services into the infrastructure means that cyber attackers have an appealing new target on the Internet. Additionally, cyber attacks are also a national-level threat that is expected to continue evolving at an accelerated pace. Therefore, implementing security countermeasures and security operations based on advanced research is important in order to protect customers’ valuable information against evolving cyber threats and to provide safe and secure cloud services. 2. R&D at the NTT Secure Platform LaboratoriesNTT Secure Platform Laboratories engages in research and development (R&D) based on leading-edge research on cryptography and malware analysis to contribute safer and more secure services provided by the NTT Group. Our basic R&D plan is to protect internal systems, the communication infrastructure, and enterprise solutions (Fig. 1). We are moving forward with R&D guided by a three-part vision: (1) coping with the most highly evolved attacks, (2) realizing safe and worry-free network use, and (3) creating new business through promoting secure use of information. We have targeted four R&D areas (Fig. 2) in order to achieve this R&D vision.
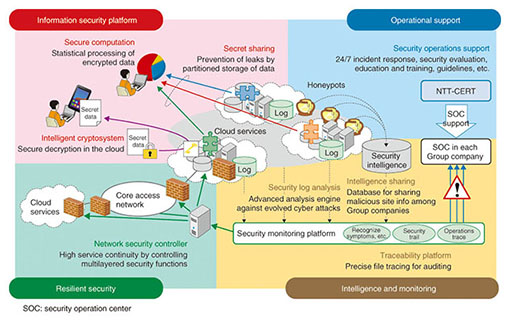
2.1 Information security platformIn the area consisting of the information security platform, we conduct leading-edge research on cryptography and develop security technologies that can protect systems and information from cyber attacks and internal fraud and also promote secure use of information. Typical technologies in this area include intelligent cryptosystems and secure computation. Secure computation technology and its evolved form, fully homomorphic encryption, are particularly suited for statistical processing, database processing, and similar types of computation while maintaining the secrecy of data stored in the cloud. The implementation of such techniques can promote not only the use of cloud services but also the creation of new business that requires the use of sensitive data such as management data and personal information. The activities in this area are described in detail in the articles “R&D on Secure Computation Technology for Privacy Protection” [1] and “Fully Homomorphic Encryption over the Integers: From Theory to Practice” [2] in these Feature Articles. For information on other technologies we are working on, please see Fuji et al. [3]. 2.2 Operational supportOur R&D in the area of operational support involves supporting security operations of NTT Group companies and improving the technology for such support. Preventing all cyber attacks is difficult because they are constantly evolving. NTT-CERT (NTT Computer Security Incident Response and Readiness Coordination Team), the CSIRT*1 organization of the NTT Group, supports security operations in both pre-incident and post-incident measures in order to respond rapidly to cyber attacks on various systems such as the cloud service system, and to minimize the damage of those attacks. For more information on the work of NTT-CERT, refer to Tanemo et al. [4]. 2.3 Intelligence and monitoringThe area consisting of intelligence and monitoring involves security visualization technologies that enable early detection of cyber attacks and provide an accurate understanding of the system status. In order to achieve early detection of cyber attacks, we research and develop technology for security log correlation analysis and malware analysis. We are also gathering information on malicious sites that infect and distribute malware and are providing such information as security intelligence to NTT Group companies. For more information on this work, please see Hariu et al. [5]. Security threats can also arise from internal fraud and operation errors, so it is important to accurately comprehend the information flow within the system in order to maintain security. Visualizing the information flow is especially important with cloud services; such visualization makes it possible to strengthen the security of cloud services and to increase the sense of trust that customers have in cloud providers. In these Feature Articles, we introduce R&D on “The TRX Traceability Platform,” which enables visualization of the information flow by collecting and linking various event logs from cloud services and other services [6]. 2.4 Resilient securityResilient security is a new area of R&D. A resilient function can avert a complete service shutdown and restore the service to a normal state, even when the service is affected by cyber attacks or natural disasters. To achieve cloud services with this resilient function, we are working on autonomous recovery technology that enables cooperation and control of virtual network technology and virtual appliance technology. The concept and component technologies of resilient security are described in the article “Resilient Security Technology for Rapid Recovery from Cyber Attacks” [7] in these Feature Articles.
3. Future studySecurity is relevant to a very broad range of areas, and some of them are beyond the scope of our laboratories. In the four areas of our R&D described above, cooperation with global organizations is important. In particular, we cooperate closely with NTT I3 (NTT Innovation Institute Inc.), an R&D facility in North America, by sharing the latest needs in the North American market and advanced technological knowledge in the cloud and security fields. We will proceed with security R&D to achieve our vision through cooperation with internal and external organizations. References
|
|||||||||||||||||