|
|||||||||
|
|
|||||||||
|
Regular Articles Vol. 14, No. 5, pp. 48–55, May 2016. https://doi.org/10.53829/ntr201605ra2 Edge Router System that Distributes Traffic Flexibly According to ServicesAbstractIn the future, communication networks will need to provide various services more flexibly and efficiently according to the diversified needs of customers and service partners. NTT Network Service Systems Laboratories is researching and developing an edge router system that distributes traffic flexibly to various service functions in a network. This system is being developed in order to reduce costs by increasing transfer capacity and reducing power consumption, and to respond to service needs flexibly by employing traffic distribution and policy control functions. Keywords: edge router system, DPI, traffic control 1. IntroductionThe Internet of Things (IoT) is a network of various physical objects—things that exchange data and have network connectivity. As IoT development has progressed and 4K/8K video has become popular, the demand for information communications has been increasing. The required quality and capabilities of communications vary widely from single very high speed sessions to numerous low speed sessions, depending on use cases, applications, and devices. In addition, for development using a B2B2X (business-to-business-to-X) business model, it is also important to provide services rapidly and flexibly according to service partners’ needs. We are researching and developing networks that have the capabilities to respond to various needs. In the NetroSphere concept [1] devised by NTT laboratories, network functions are separated into components and modules, and services are provided rapidly and flexibly by combining necessary components and modules. A key element to realize this concept is an edge router system under development that accommodates many users, classifies the service to be applied to user traffic, and distributes traffic flexibly to appropriate service functions in the cloud. This system also has a larger transfer capacity, higher power efficiency, and higher reliability than current edge routers, which will reduce network costs. Furthermore, this system has a policy control*1 function that enables new services to be provided, leading to increased revenue.
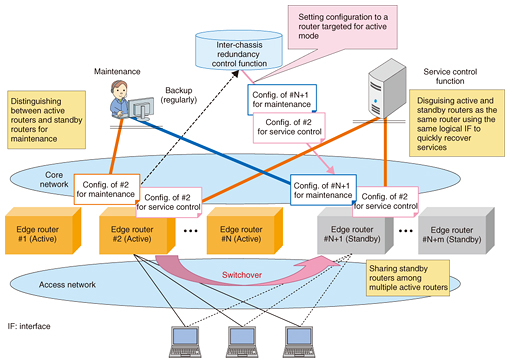
2. Cost reduction and reliability enhancement of edge router system2.1 Larger transfer capacity and higher power efficiencyThe traffic volume in communication networks has increased as the demand for video transfer services has grown, video definition has become higher, and the number of mobile devices has rapidly increased. A high performance edge router is needed in order to efficiently respond to such traffic increases. That is, the edge router system requires a large transfer capacity that supports 100-GbE interfaces and accommodates many users. This will make it possible to greatly reduce system costs and power consumption per bit or per user. Furthermore, when fewer edge routers are required in a network, we can expect a decrease in the amount of maintenance work that depends on the amount of equipment, for example, file updates and replacement of broken modules. 2.2 Inter-chassis redundancyMeanwhile, the effect of a system down failure such as a double failure of hardware modules becomes significant since systems can accommodate more subscribers than ever before. The edge routers in the system being developed have redundant module structures and redundancy in line interfaces. Moreover, this system has an inter-chassis redundancy function to achieve higher reliability. In the inter-chassis redundancy scheme as illustrated in Fig. 1, standby routers are prepared as a substitute for an active router; they provide services in the event that the active router goes down. To achieve high reliability and low cost, this scheme can adopt the N+m redundant architecture in which N active routers share m standby routers, which reduces the standby router costs.
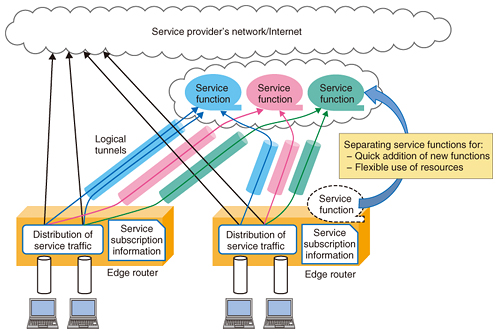
An inter-chassis redundancy control function implemented outside of the edge routers orders the edge routers to perform a switchover. The configurations of all active routers which include the information about system settings and per user settings are retained in the inter-chassis redundancy control function. In the event of a switchover, the control function sets the configuration of the active router in the standby router that is targeted for the active mode. Since the information for maintenance or system management is related to each apparatus, it is preferable to use the information that was originally assigned to the standby router. In contrast, the information for providing services such as the interfaces to the service control servers is the information that was assigned to the original active router. This enables services to be restored quickly from a system down fault. 3. Flexible addition of service functions3.1 Separation of service function from router functionIn the existing service edge router, a specific packet transfer function of each service such as the IP (Internet protocol) telephone service is implemented in a router chassis. This makes it possible to reduce the number of chassis as well as the capital expenditure. However, this implementation results in a complex packet process function in the edge router. Therefore, the number of development tasks required for deploying new service functions increases since sufficient verification is necessary to avoid degradation of other services. Furthermore, operation and maintenance work such as file updates for some services might affect the other services. We aim to introduce an isolated architecture in which service functions are separately deployed from an edge router chassis in order to enable new functions to be added easily and quickly. This isolated architecture may be especially effective in cases where rapid introduction of new functions is important and where a centralized deployment is efficient, for example, when service demand is low or highly varied. Using network functions virtualization (NFV)*2 technology to implement service functions makes it possible to reduce costs for equipment by using low-priced general-purpose servers and sharing resources among services. We plan to gradually implement an isolated deployment and virtualization of service functions. Several factors should be considered in order to determine the appropriate deployment of service functions, for example, improvement of packet processing performance in NFV and the required quality level of services. For instance, more service functions can be virtualized as the packet processing speed in virtualized functions increases and delay-sensitive services are deployed in local datacenters. 3.2 Distribution of service traffic to appropriate service functionsTo deploy service functions separately, the edge router classifies traffic according to its service and transfers the classified traffic to the appropriate service functions, as shown in Fig. 2. The edge router determines a service function in which an incoming packet is routed according to the service subscription of the user and the layer 3 and layer 4 (L3/L4) information in the packet. Then the edge router transfers the packet to the service function appropriate to each packet using logical tunnels that enable transit regardless of the destination address in the packet. In the future, we aim to achieve more flexible packet transit according to services using service chaining technology, which easily controls packets and enables them to be transferred through all of the necessary service functions.
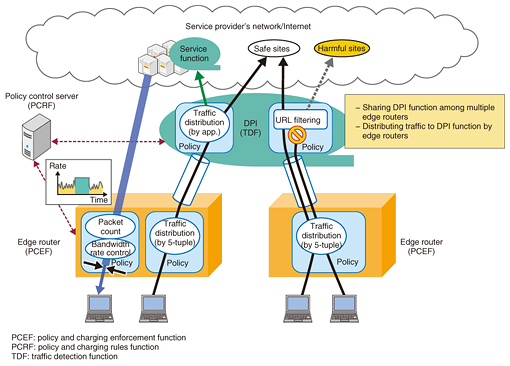
4. Function to provide value-added services4.1 Policy control by the edge router and deep packet inspectionTo provide value-added services flexibly, this system has a policy control function that can control traffic according to individual user needs and a traffic distribution function that uses high-layer information such as the kind of application, as shown in Fig. 3. Examples of use cases include bandwidth rate control depending on the amount of transferred packets, URL (Uniform Resource Locator) filtering to prevent access to harmful sites, and packet transfer to an apparatus that has a value-added function such as an optimizer to convert the bandwidth of video traffic. To provide such service processes, this system has an application based control function that uses deep packet inspection (DPI)*3 in addition to the L3/L4 based control in the edge router. The edge router and DPI have the capabilities to measure the volume of traffic, filter packets, limit bandwidth, and distribute traffic to service functions according to a policy rule predefined for each user. In the future, we aim to support dynamic setting of policy rules to change the service control depending on the state of use.
4.2 Efficient use of DPI functionThe cost per data transfer amount tends to be high in the DPI function since this function performs a complex process, that is, analyzing the payloads of packets. Placing DPI inline requires a very high performance DPI process in order to handle all transferred packets, which of course increases costs. This problem can be solved by sharing the DPI function among multiple edge router functions when only part of the traffic is the object of a DPI process such as an optional value-added service or an analysis of specified traffic. The edge router function distinguishes the packets to be processed in DPI and distributes them to the DPI function through logical tunnels. With this scheme, the cost of the DPI function can be reduced since the required throughput of the DPI function is only for processing selected traffic.
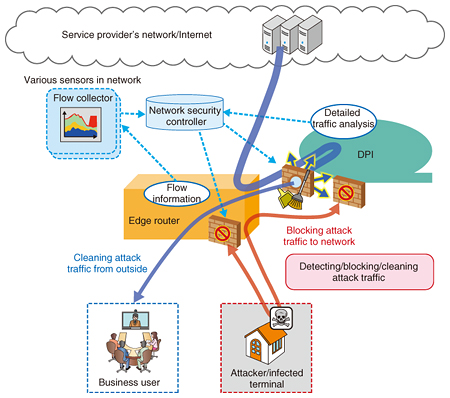
5. Extension to provide additional valueNTT Network Service Systems Laboratories is studying an extension to provide more value-added network services by combining the above-mentioned functions, that is, flexible distribution of service traffic and application based classification and control using the DPI function, with other external network functions. 5.1 Network securityOne research subject is network security (Fig. 4). The edge router filters packets to prevent unnecessary access to network equipment, giving it a network security capability. However, it is important to improve network security further as we get closer to the year 2020 since security threats are increasing year by year. We are studying features of the edge router system to be utilized in conjunction with various security devices, while still accommodating users. Specifically, those features involve sending traffic measurement data to an analyzer in order to detect security attacks and threats, distributing traffic suspected of being attack traffic to security devices by order of a security controller, and also blocking attack traffic by order of a security controller. We aim to contribute to improving network security measures in order to respond to new security threats efficiently and flexibly.
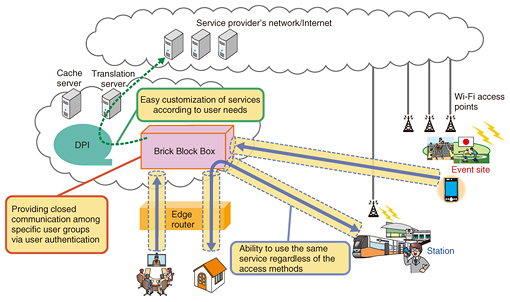
5.2 Service gateway for temporary demand for a serviceWe are researching a flexible service gateway named the Brick Block Box that can cope with temporary demand for services during events or with the various needs of corporations. We use vCPE (virtual customer premises equipment) technology, in which a communication device originally located in a user home is virtualized, to implement the Brick Block Box, which is deployed on a general-purpose server in the cloud. The Brick Block Box has location-free connectivity using secure tunnels and does not depend on a particular kind of access technology. It also features closed communication within a user group and access control so that only members of a group can access service functions in order to provide services that can easily be customized, as shown in Fig. 5.
6. Future prospectsTo achieve a network that can respond flexibly and efficiently to the needs of collaboration partners, NTT Network Service Systems Laboratories is developing the edge router introduced in this article. This edge router can flexibly distribute traffic to separately deployed service functions and perform flexible policy control per user or per application. Our aim is to provide more added value; therefore, we plan to enhance functions in order to achieve a more secure network and provide flexible services in combination with the service gateway. We are also researching ways to modularize and virtualize the edge function in the NetroSphere concept and working on developing a more flexible, highly reliable, and efficient future network. Reference
|
|||||||||