|
|||||||||||||||||
|
|
|||||||||||||||||
|
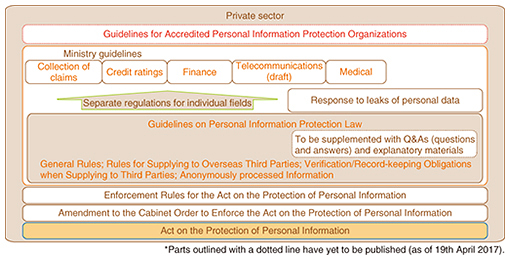
Feature Articles: Security Concerns—Growing Threats and Business Opportunities Vol. 15, No. 5, pp. 29–35, May 2017. https://doi.org/10.53829/ntr201705fa5 Key Points of the Amendments to the Act on the Protection of Personal Information, and Anonymization Methods for the Use of Personal DataAbstractThe Act on the Protection of Personal Information was amended in 2015 to promote further development of industry through the use of personal data while at the same time protecting people’s privacy. In this article, we discuss the five amendments that were made to this act. We also describe an anonymously processed information system that could lead to the creation of new business for NTT, and we introduce NTT’s proprietary Pk-anonymization technology that keeps information secure without harming its usefulness. Keywords: Amended Act on the Protection of Personal Information, anonymization methods, personal data 1. IntroductionAmid calls for rules governing the use of big data and personal data that take legal issues and privacy into consideration, the Act on the Protection of Personal Information was amended in 2015 (referred to as the amended law*1 [1] below), and government-led preparations are now being made prior to the full enforcement of this amendment on May 30, 2017. The structure of laws and ordinances relating to personal information is shown in Fig. 1. At the lowermost part of this structure, the Act on the Protection of Personal Information provides the basis for higher-level rules and guidelines, and the following items in the upper half of the structure should be seen by those trusted with personal information: Guidelines on Personal Information Protection Law [2], ministry guidelines, and Guidelines for Accredited Personal Information Protection Organizations.
Although the Guidelines for Accredited Personal Information Protection Organizations originally received a quiet reception, the new legal reforms are particularly important because they add items relating to the handling of anonymously processed information and make it obligatory for organizations to provide guidance and also include recommendations for compliance with the guidelines. The accredited personal information protection organizations*2 that apply to the NTT Group include the Japan Data Communications Association (JADAC) and the Japan Institute for Promotion of Digital Economy and Community (JIPDEC).
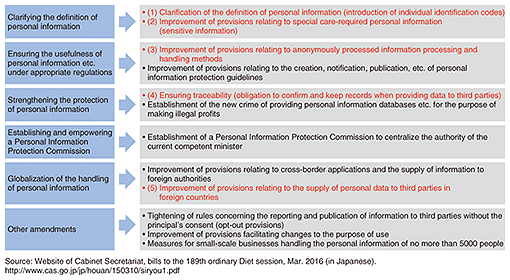
2. Key amendments to the Act on the Protection of Personal InformationWe will refer to Fig. 2, which was prepared based on government materials relating to the key amendments to the Act on the Protection of Personal Information, to describe five points that appear to have a particularly large impact on business, based on the contents of the promulgated enforcement rules and regulations.
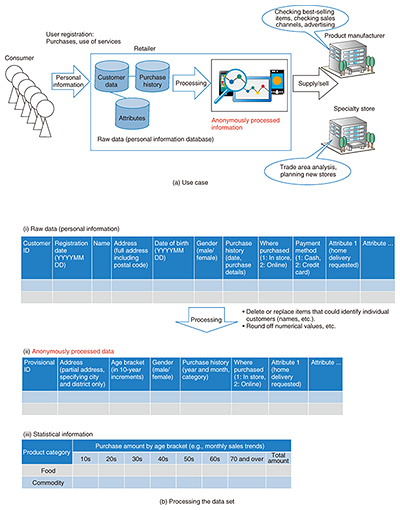
2.1 Clarification of the definition of personal information: introduction of individual identification codes (amended law, Article 2, Paragraph 2)The concept of individual identification codes was introduced as a way of identifying specific individuals in a set of information so that personal information could be referenced without using a person’s name or other details. Specifically, it includes biometric information such as fingerprint/face authentication data and vein pattern data, My Numbers (social security/tax numbers), passport numbers, driving license numbers, and pension account numbers. For example, an individual set of fingerprint data for authentication stored inside a smartphone or USB (universal serial bus) memory stick with a fingerprint authentication function constitutes personal information, thus making it necessary to check the provisions regarding how this information is handled by businesses. 2.2 Personal information requiring special care (amended law, Article 2, Paragraph 3)Personal information that must be handled carefully typically comprises information that would be liable to cause discrimination and/or prejudice if mishandled. This includes sensitive information such as the principal’s race, creed, social status, and medical history. Since the introduction of this amendment, personal information that must be handled carefully can no longer be handled without consent, so it is necessary to obtain in advance a principal’s consent even for simple workplace health questionnaires and the like. 2.3 Anonymously processed information (amended law, Articles 36–39)The amended law defines anonymously processed information as information that has been processed to make personal information impossible to identify a specific individual, and from which it is impossible to restore this person’s personal information, and a system where this information can be distributed subject to certain regulations. When supplying personal information to a third party, it is necessary to obtain the principal’s consent, but anonymously processed information has the advantage that the principal’s consent does not have to be obtained. 2.4 Ensuring traceability (obligation to confirm and keep records when providing data to third parties) (amended law, Articles 25 and 26)A service provider that receives personal data from another party is subject to various obligations including confirming the background of what was transferred, and keeping records including the items of information that were transferred, and when the transfer took place. This is intended to ensure that personal information obtained and divulged by illegal means is prevented from circulating endlessly. This requires checking whether an existing contract has been commissioned or has third-party provisions, and if necessary adding log acquisition functions. 2.5 Provision of personal data to third parties in foreign countries (amended law, Article 24)A third party in a foreign country is defined as a person or persons (including corporate bodies) located in a foreign country (but not a company’s foreign branch offices or the like). When personal data are provided to a third party in a foreign country, it is in principle not possible to do so without the principal’s consent. This consent must be obtained even when entrusting employee information to a cloud service provided by a foreign entity. Exceptions to this rule include businesses in countries designated by the Personal Information Protection Commission, and businesses that have been certified based on the APEC Cross Border Privacy Rules (CBPR) system, for which consent is not required [3]. 3. Creation of new business through the use of anonymously processed informationAnonymously processed information is information related to an individual that has been processed to protect people’s identities from being disclosed. It has the advantage that the principal’s consent is not required when the information is provided to a third party, and it is therefore expected that new business will be created to take advantage of this feature. Some use cases of anonymously processed information are illustrated in Fig. 3. When a consumer registers with a retailer in order to access services or purchase goods, the retailer stores raw data such as the consumer’s customer data and purchase history. The retailer might choose to process these raw data and supply or distribute the processed data so that other people can use them to identify best-selling items, analyze sales channels, or plan the opening of new stores. It is possible to use data anonymization for this subject.
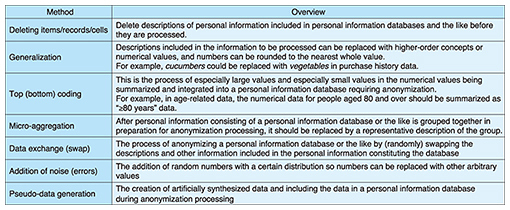
Possible ways of processing these data are shown in Fig. 3(b). In table (i), the retail operator manages users according to their customer identifications (IDs) and records each customer’s registration date, name, address, date of birth, and gender. Furthermore, each customer ID is associated with information including a purchase history (date, purchase details, amount paid), where purchased (in store, online), payment method (cash, credit card), and whether or not a home delivery service was used. Under the current law, this information might have been provided to product manufacturers in the form of statistical information as shown in table (iii), but one might consider processing these data in such a way that they contain slightly more detail without revealing any personal information. As in table (ii) above, the information is processed so that it can be used to find out how many products in a particular category were purchased during a particular period, and whether they were purchased in store or online. To avoid identifying individuals, the number of purchases is rounded, and any information that could be used to identify someone (such as their name or address) is deleted. The processed data are expected to be used for marketing purposes such as allowing product manufacturers to check the performance of strong sellers, or finding out if a product category of interest has been accepted into the envisaged customer layer, or whether or not home deliveries are popular. 4. Anonymization methods we have developedIn anonymization processes according to the amended law, personal information is required to be processed so as to make it impossible to identify specific individuals. Since it is very difficult to prove that a specific individual cannot be identified, the guidelines [4] state that in practice, rather than requiring the elimination of all technical possibilities of identifying a person by any means whatsoever, it should at least be impossible for a personal-information-handling business operator or an anonymously processed information-handling business operator to identify a specific individual using ordinary business skills and methods. Specific methods and standards for anonymization processing are to be determined separately for each industry according to the abovementioned detailed regulations and guidelines. For example, in the anonymously processed information guidelines [4] and the Anonymously Processed Information Creation Manual [5], methods such as top (bottom) coding and noise addition are presented (Table 1). In practice, when these methods are used for anonymization processing, it is necessary to study what sort of processing methods should be applied by clarifying the use cases of personal data, and identifying the risks of outcomes such as the identification of individuals by partitioning the data items according to identifiers, attributes, and history.
To use these data for actual business, in addition to ensuring that they are anonymized and do not allow the identification of individuals, there is also a greater need to process the data so that they can be used effectively. At NTT Secure Platform Laboratories, we have developed an anonymization method based on NTT’s own evaluation measure called Pk-anonymity where the evaluation measure of k-anonymity is replaced with a probabilistic measure [6]. This is the first ever method that introduces randomness by stochastic rewriting of item values, which has been mathematically proven to have a level of security equivalent to that of k-anonymity. In anonymization based on Pk-anonymity, the values are stochastically rewritten and are thus different from the original data, but can be processed into data that are statistically close to the original data by using a probability-based method called Bayesian inference. A processing method called generalization is often used in k-anonymization. For example, the word cucumbers might be changed to vegetables in order to change the level of detail in the data. However, in Pk-anonymization, the data are rewritten without changing the level of detail. For example, cucumbers might be changed to tomatoes. It is thought that this method could be useful for the analysis of marketing data or the like where people want to see detailed data distributions. At NTT Secure Platform Laboratories, we are preparing to provide services to tie in with the enforcement of the amended law by continuing to research and develop anonymization methods such as these, by participating in joint research initiatives and verification trials together with businesses that actually use this sort of data, and by taking part in national contests related to anonymization methods in order to gather technical know-how related to the anonymization of diverse types of data. 5. Future prospectsAs progress is made with the related guidelines of the amended law and revisions to the Guidelines for Accredited Personal Information Protection Organizations, we also plan to review the provisions related to the protection of personal information by businesses, and to investigate business models that make effective use of anonymized data. In line with current trends in legal systems, we will continue to support the NTT Group in both legal and technical aspects and continue to take part in external activities including academic activities. References
|
|||||||||||||||||