|
|||||||||
|
|
|||||||||
|
Feature Articles: NTT R&D Forum 2018 Autumn Special Sessions Vol. 17, No. 3, pp. 27–34, Mar. 2019. https://doi.org/10.53829/ntr201903fa5 
Co-innovating to Accelerate Transformation and Create New ValueAbstractDimension Data, an NTT Group company, recently opened its first Client Innovation Centre (CIC) in Sydney, Australia. This article introduces the CIC and presents examples of co-innovation generated at CIC between Dimension Data, their clients and partners, and the NTT research and development (R&D) laboratories. This article is based on a speech given by Debra Bordignon, Chief Technology Officer, Dimension Data Australia, at NTT R&D Forum 2018 Autumn on November 29, 2018. Keywords: co-innovation, digital transformation, security, disruptive innovation, exponential technologies 1. Client Innovation CentreOn August 1, 2018, we opened the first Client Innovation Centre (CIC) in Sydney, Australia [1]. Our team created this center as a facility and as an engagement model for innovation with our clients, and we run this as One NTT. The purpose of CIC is to engage with our clients in co-innovation to accelerate their transformation in this digital era and to help them achieve new purpose and value. It has come about through the close relationships and collaborations we have with the NTT research and development laboratories (NTT R&D). Our clients are curious and expectant around One NTT. Our clients are successful organizations, mostly with a rich analog heritage and assets. All of our clients are transforming their business to flourish in new times. Generally speaking, they are dealing with a legacy underbelly of brittle technologies, processes, and culture. They are hoping for a deeper conversation with us about more strategic levels of innovation. They want us to step up to help them accelerate their journey towards digital transformation, as the integrator and manager of their digital estate. They are looking for opportunities to differentiate themselves in changing markets, through applied innovation with the ecosystems we can bring together, including the wonderful assets that we can bring from NTT R&D. In some cases, we are looking to co-create new value and jointly commercialize new solutions that can advance the digital economy and benefit society (Fig. 1).
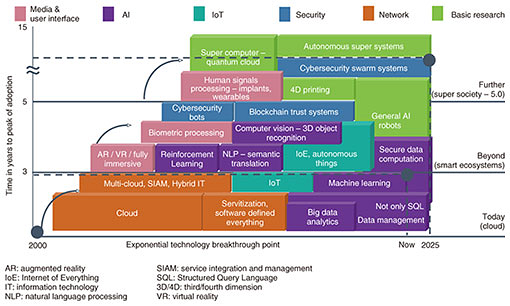
It is a completely immersive experience that we have created with our CIC model, and we are not only bringing clients into this, but also creating complimentary industry forums to address some grand challenges together at a sector level. 2. Vision of societyIt has been four months since we opened the CIC, and we are already well engaged in purposeful innovation with numerous clients. The use cases that feature cutting-edge technologies from NTT R&D are provoking new thinking and intentions. Yet we are not merely bringing in R&D technologies from Japan; very importantly, our CIC is modeled on the ethos of Society 5.0 [2] and NTT’s expression of that through the business-to-business-to-X (B2B2X) model for value creation. We feel that it is a really important time in the world today to bring a moral and ethical framework to the way that technology is used to shape future society and humanity, and Society 5.0 is something the whole world should be considering. We need a vision for society because that provides the compass settings for what we are innovating towards. If we look at what’s happening today, we see there is an explosion of applications and interfaces, mixed reality experiences, growing intelligence all around us, hyper-connected people and things. And data fuels the expansion of digital frontiers. All these changes are built upon the foundations of the Internet, mobility, social, cloud, and digital platforms. However, what’s coming in the next 15 years is very different. In 15 years’ time, we will look back and recognize that today was really just the toy box of digital infancy. What will the world look like in 15 years? It will be a profound convergence between the physical and the cyber worlds where the interface will become us. Our gestures and our movements and thoughts are the data and application programming interfaces (APIs), and all the simplification of our experience will entail profound complexity under the covers. Dynamically driven from an intelligent edge and completely trustless, systems of record, systems of engagement, and systems of intelligence will follow architectural conventions that have not yet come about. Powering all of this will be, literally, a quantum change. This is the compass that we use for guiding innovation today, and when we take hops, steps or leaps forward with our clients, it’s referencing scenarios from this future vision. 3. Transformation and innovation themesAt this NTT R&D Forum, we are experiencing a lot of amazing emerging technologies and the use case stories provided by the NTT R&D researchers suggest some practical applications. The Forum themes are media & user interface, artificial intelligence (AI), Internet of Things (IoT), security, network, and basic research, and each category provides numerous use cases to explore what NTT has to offer towards this future vision. We created a mapping that helps unpack what types of technologies are coming together and when and how they are maturing (Fig. 2). On the X-axis of this map is the actual point of a technology breakthrough where the linear improvements become exponential, and then it suddenly becomes possible to create commercially viable solutions from those maturing technologies. The Y-axis is the peak of the innovation adoption curve, which means the time when the adoption of solutions transitions from the early to the late majority.
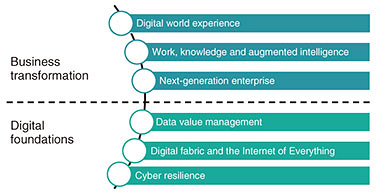
Now, in our CIC, acting as One NTT, we are looking to work with technologies that can deliver value from now into the next five years. There are two types of innovation we conduct. One of them is working in this bottom line here of connecting the dots of all the technologies that are mature today but have not yet been joined together to create a simplicity and agility that help our clients to speed themselves up to be able to move to the next horizons. That’s not always exciting as innovation, but it is very important. The other area is to choose emerging technologies in this new category of beyond and to be able to accelerate the maturation and their early adoption into markets to create differentiation and a competitive advantage for our clients. That is our appetite of innovation through CIC. Regarding digital transformation, every organization is intent on this, but I don’t think it’s universally agreed what it means. What does it really entail? Across our group, we have combined our research and collective experiences working with client organizations globally. We have identified six key business performance areas and within each of these, the capability investment intentions of businesses to achieve cohesive and sustainable success. All of this totals to a 3.9 trillion US dollar global investment in technology enabled transformation across 2020 (Fig. 3).
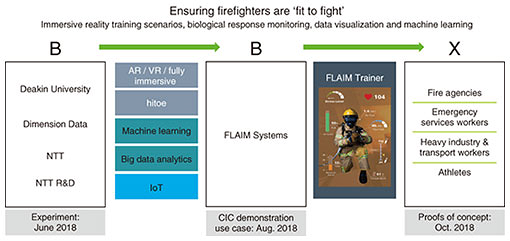
It is important to consider your overall business transformation and innovation goals against these performance areas and capabilities—do you have gaps, are you underinvested in some areas, where will you most benefit from acceleration or disruption? On this basis, what are the innovation priorities and how will we target and measure value? Let me briefly explain what we mean by these capability investment vectors. The three in the bottom part of the figure are about establishing the digital foundations for an enterprise, the capabilities needed to participate in digital economics. The three in the upper part are about your transformative capabilities—what you do to achieve new purpose and create new value and prosperity for your organization. In a little more detail, at the very bottom, we have cyber resilience, the ability to create a new DNA of cyber resilience, embedded in technologies, processes, practices, and culture. Digital fabric and the Internet of Everything is the shift in information technology (IT) to hybrid infrastructures matched to business performance needs, the marriage of IT and OT (operational technology) systems through IoT and the transformation of the IT organization from a cost center to business enabling services. Then, there is the area of data value management, which is essentially the digital heart transplant that most organizations truly need for data to become the lifeblood of the intelligent, digitally orchestrated enterprise and to become a valuable asset on the balance sheet. In terms of business transformative capabilities, the first is the next generation enterprise. This entails the transition from relatively static and linear supply chain models to dynamic ecosystem business models. The technology re-platforming entails software defined and data driven APIs orchestrating these ecosystem flows. Work, knowledge, and augmented intelligence is about enabling knowledge workers to be their most effective selves, whether as creators, communicators, managers or decision makers, in the way they work with each other, visualize and use data, train their cognitive agents to support what they do. Finally, digital world experience is about the stakeholder and the changing nature of their expectations and their experience with your organization. The shift in focus from omni-channel to channel-less as digital becomes ambient within the atmosphere. And we are increasingly interacting with our stakeholders’ AI agents and their personal data APIs. These six vectors map to the future society view. Very often we find that our clients do not have such a cohesive approach to their transformation. Through the CIC model, we can help identify gaps, and direct innovation accordingly. 4. Benefiting from NTT R&D innovationsNow I would like to share with you two examples of what we have been able to create through our relationship with NTT R&D and our clients and partners. They illustrate the coming together of the right partnerships and interesting collective mixes of capabilities under the B2B2X model. We have the B2B of NTT R&D, ourselves and our university clients and partners, the NTT operating companies in the region, and of course the X, end user beneficiaries. It is the one plus one equals many more than three phenomenon that is occurring here. Our collaborations and flows are becoming much more bi-directional with NTT R&D because we are bringing the use cases from industries and clients in markets that the NTT researchers find stimulating and that add to their thinking about their research projects. Indeed, we are also generating new intellectual property (IP), which we share back with NTT R&D. So it is a growing relationship of value co-creation. 4.1 FLAIM TrainerTMThe first example is FLAIM TrainerTM [3] (Figs. 4 and 5). I would like to share with you the story about how this has come about because it’s interesting to understand. Deakin University is an innovative university in Australia, they have a strong commercialization track record from their R&D. In the middle of 2017, they had created a solution called FLAIM Trainer, which is a virtual reality (VR) and haptics based firefighting solution with numerous simulator scenarios such as cars that are on fire, jets on fire, and other situations. Deakin University is also a close client/partner of Dimension Data Australia. In July 2017, we brought some members of Deakin University to the NTT R&D labs in Japan and explored a wide range of emerging technologies. Everything starts by focusing on something specific, and we felt immediately that there was a great opportunity to enhance what they had created with FLAIM Trainer by adding the ability to biometrically monitor firefighters during their training.
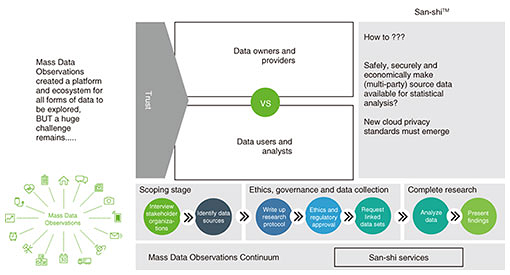
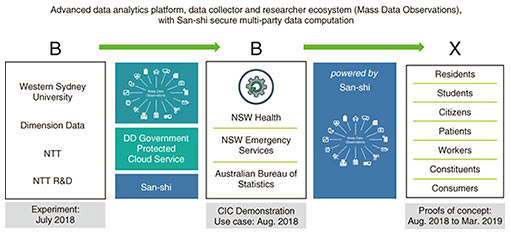
So the idea of bringing FLAIM Trainer together with the NTT hitoeTM biosensing technology and our Dimension Data Australia data and analytics expertise was born. We started the prototype process, which Dimension Data managed, and very quickly we were able to create a solution which included electrocardiogram (ECG) sensing married with the VR experience, providing real-time visualization of the physiologic response alongside the environmental data about fog and temperature, and pressure flows from the hose. We brought this to the NTT R&D Forum held in February 2018. This created a lot of interest. FLAIM Systems Pty Ltd. (a start-up wholly owned by Deakin University), meanwhile, raised funds to commercialize its core offering. We suggested to NTT R&D that this solution would indeed be greatly enhanced and would be unique in the market if we added in the ability to sense electromyography (EMG) muscular activity. NTT R&D agreed, and joint research has been undertaken by NTT R&D and Deakin researchers. We are now adding EMG capability into the hitoe sensing and the data platform solution. This will improve the ‘fit to fight’ insights and training approaches for fire departments and broaden applicability to other industries such as defense, ambulance, and heavy industries with safety issues for workers. This use case has seen a relatively rapid translation to value, characterized by true collaboration and flow of IP in both directions. Most importantly, we have retained line of sight of B2B2X and the importance of taking a market focus. 4.2 Mass Data Observations and San-shiTMNow I’d like to share with you another example. This co-innovation has come about between NTT R&D, Western Sydney University, and Dimension Data Australia. This use case demonstrates two things: firstly, ways of bringing many forms and sources of data together to be able to use it for research purposes; but as well, with the addition of San-shiTM, NTT’s secure computation system, the potential to drive new standards in cloud data privacy and enable safe data sharing, which is demonstrably lacking at the moment in the world (Figs. 6 and 7).
Firstly, the journey of this co-innovation. Western Sydney University and Dimension Data have co-created a platform called Mass Data Observations. It is a large-scale data management platform that can accept all forms of data for exploration by researchers in projects that may be open and collaborative or discrete and privately conducted. In addition to this, the Mass Data Observations platform enables researchers to crowdsource research challenges and attract interest from people who may wish to collect data for them or become subjects in research projects. Both the researchers and the data contributors on this platform can be rewarded in RiByts, research incentive bitcoins. The idea is to drive a large-scale collaborative data-driven research ecosystem. In July 2017 we brought some top researchers from Western Sydney University to NTT R&D labs in Tokyo, and just as with Deakin, we saw many things we would like to work with, but immediately we were struck by what we saw with San-shi, the prototype of a secure, multi-party data computation platform. In our view this was cutting-edge and potentially world-leading in the area of encrypted data analysis and secure multi-party data computation. Given our enthusiasm and our access to test high value use cases with industry partners in Australia, NTT R&D agreed to accelerate the English version of San-shi. By January 2018, a cohort including experts from my team, Western Sydney University, as well as Deakin University, returned to Tokyo for knowledge transfer and we brought San-shi back to Australia, integrating it with Mass Data Observations, running on our cloud platform in Australia. We immediately started exploring and testing the capabilities and running use cases through it. The following use case is one of those examples. Mass Data Observations is a powerful platform for bringing all sorts of data together to enable exploration of data. However, the challenge still remains, that when it comes to bringing sensitive data sets together from multiple parties, we have a serious issue with trust and quite rightly so, and this creates barriers to approval by ethics and governance committees, as anyone who does research knows. Therefore, the question is how to safely, securely, and economically make these data sets available for analysis. That’s where we brought San-shi into the equation. Data about fires in the state of New South Wales had never been brought together before to understand what the full social, economic, and health impacts of fires were, let alone trying to improve the outcomes. Ten million people live in the state of New South Wales. Before this research was conducted, data recorded that there were about five fires a day. In fact, there were 20. Deaths attributed to fires were about 500 over a 10-year period, but it was found that there were actually 9000 deaths. The emergency departments reported a couple of dozen injuries from fires a day, but in fact, there were over 213. So clearly, there were sources of information everywhere, and this information was never brought together to create a very clear picture of the impact of fires. Researchers at Western Sydney University had researched this in the traditional way, spending three years and hundreds of thousands of dollars gaining ethics clearance and bringing together 11 different data sets, from the fire department, first responders, hospitals, register of deaths, primary care providers, insurers, and others. We set out to show that the use of Mass Data Observations with San-shi created a ‘trustless’ technology environment that could execute this challenge accurately and without the potential of breaches. This is important as in the future, this may reassure ethics and governance committees, expediting approval processes and affording significant time and cost-savings for sensitive multi-party data research use cases. I will briefly explain how San-shi works. Eleven different sources of data were available; when they are ingested into San-shi, each data source is encrypted and split across multiple servers. It never exists inside the San-shi system in its original form. When a researcher wants to access that data to conduct statistical analysis, the data are brought together but never decrypted; they’re analyzed in an encrypted state. The analyst never receives the source data; they only ever receive the output. The data sources are never held in their original state by San-shi, and the data are never actually touched by researchers—this is trustless secure multi-party computation [4]. Just think about what new value can be created from such a capability, unlocking research possibilities previously deemed not safe to conduct. In this use case about the impacts of fires, we can create new citizen services where people could check the safety records of buildings and certain appliances, and first responders would know much more about the spectrum of impacts from a fire and adopt the best choice of interventions. Indeed, firefighters could improve their training regime, and the government could enforce much better policies and public awareness around fire safety. Thus, this use case has been illustrative and powerful for us, and we are now exploring more use cases around San-shi, notably in healthcare policy and population-wide interventions. 5. SummationThese examples illustrate why we created the CIC and what outputs are being generated. We now have interest from other parts of the global NTT family, to use the CIC model as a template for engaging with NTT R&D, using B2B2X to drive strategic engagement in their markets and with their clients. Returning to my opening remarks about what our clients and partners want from One NTT and an innovation relationship—to accelerate transformation, to differentiate and lead in their markets and/or to create new value through partnership—we are stepping up to this expectation, learning, and evolving with our clients. If you are curious about these individual experiments but also the CIC model and the potential flows from research to innovation to commercialization, then please come and talk to us at our booths at this forum. I leave you with a question. When you think about your organization’s transformation and innovation needs, what would or could you want from a truly One NTT? Because when we bring this all together, what can be harnessed for you is truly amazing. References
Trademark notesAll brand names, product names, and company/organization names that appear in this article are trademarks or registered trademarks of their respective owners. |
|||||||||