|
|
|
|
|
|
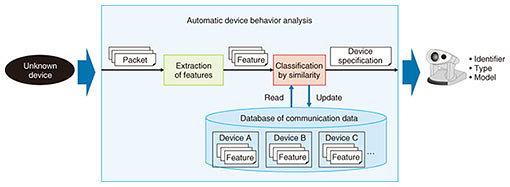
Feature Articles: Network Technology for Digital Society of the Futureˇ˝Research and Development of Competitive Network Infrastructure Technologies Vol. 17, No. 6, pp. 33–36, June 2019. https://doi.org/10.53829/ntr201906fa10 Per-device Policy Control Technology Using Artificial IntelligenceAbstractThe number and variety of Internet of Things (IoT) devices such as network cameras and televisions connecting to networks has been increasing recently, and the network requirements for each of these devices are also diversifying. This article introduces policy control technology for controlling networks in the IoT era that is optimized for each device by automatically identifying the type and/or model of each device from its communication behavior. Keywords: IoT, policy control, device identification 1. IntroductionThe development of the Internet of Things (IoT) is continuing, with all kinds of objects connecting and communicating with networks. As this development progresses and 4K/8K video gains popularity, new usage scenarios and applications are emerging, and the devices being used are becoming increasingly diverse. The quality requirements and communication characteristics are also becoming more diverse, for example, high-speed and high-capacity transmission, or low-capacity but capable of transmitting many sessions. NTT Network Service Systems Laboratories is conducting research and development on a policy control technology for the IoT era for implementing network control optimized to the type and characteristics of each device connected to the network that flexibly handles the network requirements as devices increase in capacity and diversity. We introduce here the overall system and two of its component technologies. 2. Policy control technologyThe policy control technology identifies the traffic from an application or particular user and controls traffic according to individual control rules (policies) based on the results, to provide flexible, value added services that meet the diverse needs of users. Examples of types of control include filtering, quality of service, and bandwidth control. The policy control technology is implemented by two main functions called the Policy and Charging Enforcement Function (PCEF) and the Policy and Charging Rules Function (PCRF), and these are located within the carrier network. The PCRF decides which policies to apply based on the user or application, and the PCEF executes control instructions. The PCEF identifies input traffic and applies appropriate control according to instructions from the PCRF. 3. Automatic device behavior analysisWe have been developing a means of automatic device behavior analysis. It identifies the type and model of a device based on communication data. For example, it can identify network cameras and displays on a home or office network. Identifying the type of a device makes it possible to optimally operate networks and efficiently manage huge numbers of devices. The automatic device behavior analysis does not require high performance computers or special software because it only uses ordinary communication data from devices. The technology performs two stages of processing (Fig. 1): extraction of features from communication data, and classification based on the similarity of features.
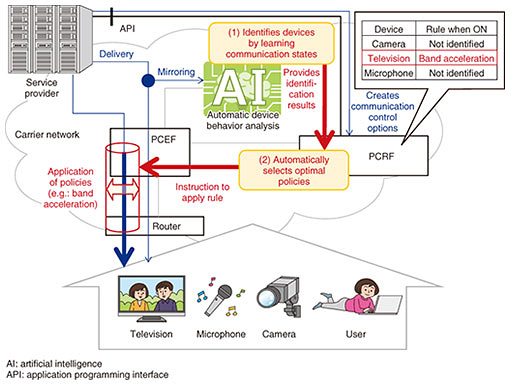
In the first process—extraction of features—the system collects packets from a device at regular time intervals and creates abstracted data from it using information such as the packet length and the number of packets. The abstracted data are used as device feature data in the next process. In the second process—classification based on similarity of features—the system compares feature data prepared for each device type and model with the feature data from devices to be identified, to determine which is most similar. This process uses machine learning to derive similarity of devices from large volumes of feature data. This processing enables the system to identify the type and model of devices. 4. Overall systemWith conventional policy control technologies, control is performed at the level of subscriber lines. For this reason, individual devices cannot be identified from the network side if a subscriber line accommodates multiple devices. Therefore, we added a way for the PCRF to automatically analyze behavior and select policies for each device from the device identification results. The overall architecture of this system is shown in Fig. 2. Specifically, an artificial intelligence (AI) component with the automatic device behavior analysis is placed on the carrier network, mirrored packets are input to the AI, and (1) device types and models are identified by the automatic device behavior analysis. After the identification by the AI is completed, the PCRF is notified of the subscriber line information (source IP (Internet protocol) address etc.) and corresponding results, and (2) the PCRF uses this information to automatically select optimal policies from per-device policies associated with the subscriber line prepared beforehand. The PCRF then instructs the PCEF to apply the relevant policies to communication from each of the devices.
Use of this technology allows individual devices on a subscriber line to be identified, and network control that is optimized for each device to be implemented. 5. Future prospectsWith the increasing number and diversity of devices connected to networks, we have introduced automatic device behavior analysis, which identifies the types and models of devices from their communication behavior, and policy control technology, which implements network control optimized to each device, based on this information. Various methods are possible for creating feature values from communication data and for determining similarity in the automatic device behavior analysis, so we will continue working to improve the technology and create services, keeping in mind the networks to which it will be applied. For the policy control technology, service providers providing services to users will continue to study design and configuration of new per-device policies, and we are studying an application programming interface that will enable flexible provision of services. |
|