|
|||||||||||||||||||||
|
|
|||||||||||||||||||||
|
Feature Articles: Network Architecture in the 6G/IOWN Era: Inclusive Core Vol. 22, No. 12, pp. 33–39, Dec. 2024. https://doi.org/10.53829/ntr202412fa3 Self-sovereign Identity (SSI) Infrastructure for Reliable Identity Data Distribution in the 6G/IOWN EraAbstractThe trend toward digital identity is accelerating, whereby user identity data are digitized in a standardized format so that they can be used by a wide variety of services. NTT Network Service Systems Laboratories is engaged in the research and development of the self-sovereign identity (SSI) infrastructure that enables the linkage of network services and digital identity as an elemental technology of the Inclusive Core, which is a network architecture for the era of 6G (6th-generation mobile communication system) and IOWN (Innovative Optical and Wireless Network). This article describes the trends related to digital identity and explains the SSI infrastructure, including the use case demonstration of applying it to the metaverse. Keywords: digital identity, self-sovereign identity, fixed-mobile convergence 1. What is digital identity?A digital identity is a set of personal attribute information used to distinguish an individual from others. Why is digital identity attracting so much attention? In the real world, a person is identified by another looking at their face or by them presenting an identification card to prove that they have a certain nationality or that they have a certain qualification. We believe that digital identities are attracting attention to meet the needs of digitization to provide various services online and confirm the attributes and qualifications of each individual to use services provided in the digital space more safely and conveniently. After describing the trends surrounding digital identity, we introduce the self-sovereign identity (SSI)*1 [1] infrastructure, an elemental technology of the Inclusive Core, which is a network architecture that NTT Network Service Systems Laboratories is researching and developing for the six-generation mobile communication network (6G)/Innovative Optical and Wireless Network (IOWN) era.
2. Trends in digital identity2.1 European UnionIn the European Union (EU), the development of digital identity products and standards is progressing, particularly in the development of legislation and provision of services. 2.1.1 Widespread use of electronic identification (eIDAS regulation)In the EU, the eIDAS (Electronic Identification, Authentication and Trust Services)*2 regulation has been introduced [2] to provide a framework that enables mutual authentication of electronic identification cards issued in different EU member countries (Fig. 1). This enables EU citizens to securely use digital services across borders. An update called eIDAS 2.0 proposes that users can manage their digital identity information and that this can be achieved through a wallet service called European Digital Identity Wallet. This update was officially approved in February 2024.
2.1.2 Introduction of electronic passportsMany EU member countries issue electronic passports, which hold digitized personal information using biometrics or RFID (radio frequency identifier) chips. This simplifies border crossings and the use of online services. 2.1.3 Expanding use of electronic identificationIn many EU member countries, the use of eID (electronic identification) for tax reporting and administrative procedures has become commonplace. This enables individuals to securely identify themselves online and conduct transactions across national borders between EU member countries. 2.2 U.S.In the U.S., the following trends in digital identity are occurring and attracting attention worldwide. 2.2.1 Promotion of digital identificationDigitalization of driver’s licenses and identification cards is progressing in each state. In some states, digital driver’s licenses are available through mobile apps, making online identification easier. 2.2.2 Introduction of digital health passportThe COVID-19 pandemic has increased the demand for digital health passports. In the U.S., efforts are underway to electronically manage and certify vaccination certificates and health status. 2.3 JapanIn Japan, there have been various developments related to digital identity.2.3.1 Spread of My Number cardsA My Number card is assigned to each citizen and resident, and each citizen/resident is required by law to have a personal number (My Number). This card can also be used online, enabling the use of various administrative services and electronic applications. 2.3.2 Spread of digital certificatesDigital certificates are widely used by companies and government agencies. They are used for digital signatures and online procedures and have legal validity. The shift from paper certificates to digital certificates is progressing with the use of digital signatures, electronic contracts, and anti-counterfeiting certificates for software. These trends confirm that digital identities are becoming increasingly popular in Japan, their convenience is being recognized, and that digitalization of identities is progressing in various government services and in daily life.
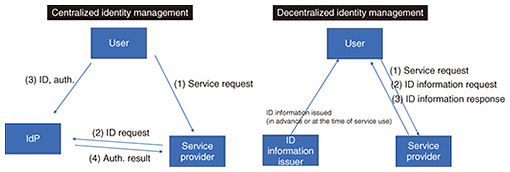
3. Technology trends in digital identityNext, we discuss important technology trends related to digital identity. 3.1 Popularization of SSISSI is a concept that enables users to control their identities. This approach enables individuals to have their own digital identity, i.e., a personal identifier (ID) and associated personal information such as attribute information and various certificates, without depending on a central administrator or third party. 3.2 The rise of decentralized identityA decentralized identifier (DID)*3 is a form of digital identity that is managed by users, rather than by a centralized system [3]. It is often based on distributed ledger technology (DLT), such as blockchain, enables users to own and manage their data, and is an elemental technology for SSI. DIDs are becoming increasingly popular, with standards organizations such as the World Wide Web Consortium developing related standards. 3.3 Development of verifiable credentialsA verifiable credential (VC)*4 is a mechanism to securely receive certificates and information issued by various institutions and services and to link them to one’s digital identity. For example, degree certificates, medical records, and membership cards can be issued as VCs and submitted to third parties when necessary. VCs enhance the system in which data ownership and privacy are managed by the users and are often used in conjunction with DIDs, which are also an elemental technology to actualize the concept of SSI. As shown in Fig. 2, centralized identity providers (IdPs) had managed identity information and the data associated with it, and the transfer of data was provided from IdPs to the service providers that use the data. In distributed identity management, data are managed by the users and presented to the service providers they use. This is called decentralized identity management because user data are not collected in one place but managed by each user and is attracting attention as a method for promoting the distribution and utilization of digital identity information while preventing the leakage of user privacy information.
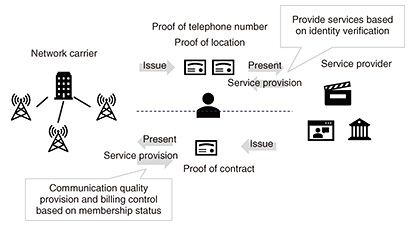
4. Digital identity and network services in the 6G/IOWN eraVarious use cases using DIDs and VCs are being studied and demonstrated in line with these legal and business trends as well as with the progress of standardization and other technological establishment. Each industry is currently studying how to use digital identities, including DIDs/VCs. However, the use of digital identities is not limited to each industry but will bring about greater benefits, such as improved convenience and operational efficiency, only if it is promoted across industries. In other words, each industry will determine what digital identities can be issued and used, and the information issued by each industry will be used across industries. It is expected that the usage scenes will expand not by summing up but by adding up. The trend toward digital identities for network carriers has only just begun to be discussed by several organizations. NTT Network Service Systems Laboratories, as a network carrier, is committed to the development of digital identities and is studying technologies to achieve digital identity information distribution contributing to the development of services based on such information. NTT Network Service Systems Laboratories is also studying the provision of network services using digital identity information distributed in society. The following is the status of these studies. 4.1 Publishing digital identity informationNetwork carriers, both mobile and fixed, play a variety of roles in the digital society. The provision of communication services, such as data communication and telephony, are the main services provided, and when providing these services, KYC (know your customer) and residence verification are conducted to ensure that communication services are provided to the right users without error. For users of telephone services, a telephone number is assigned, and the subscriber is guaranteed to be able to use that number. For cell phone users, communication services cannot be provided without knowing the location of the user; therefore, the location of the user must be known at all times as long as the user is in a place where communication is possible. Contract information and information required for service provision are usually held and managed internally by the network carrier. Issuing this information in a reusable form to users and other service providers may add value to the network. For example, by issuing a VC as proof of possession of a phone number, it is possible to provide a highly reliable and verifiable certificate as contact information for the various services that currently require the input of contact information (Fig. 3). Not only phone numbers but any information presented to the network carrier when subscribing to a communication service can be issued and distributed as digital identity information of the user, which is verified by the network carrier. For example, when a user wants to withdraw money from a bank account at an automatic teller machine (ATM), it is possible to check whether the person operating the ATM is really at that location if the bank account and cell phone contract are linked in advance, making it possible to prevent a person other than the user from withdrawing money. This will make it possible to prevent the withdrawal of money by someone other than the authorized person.
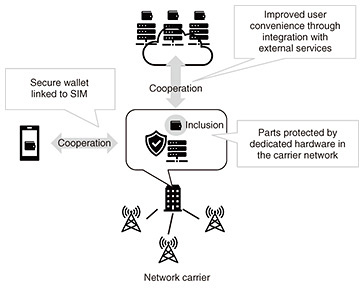
GSMA (Global System for Mobile Communications Association) and other organizations have started discussing this kind of initiative [4], and the issuance of digital identity certificates by various network carriers is expected to accelerate. NTT Network Service Systems Laboratories will work on standardizing certificates that can be issued by various network carriers and demonstrate use cases using such certificates. 4.2 Secure ID WalletDigital identity information is managed by the user, and the user decides where and what to present. However, such information is important for both the user and service provider that uses it, and it is necessary to prevent data leakage, falsification, and unauthorized duplication, transfer, or other misuse by the user. Therefore, it is necessary to have a mechanism to protect data from attacks such as malicious software installed on the terminal where data are stored and data in the terminal’s wallet are stolen. It is also necessary to address the risk of data loss if a user loses their terminal. NTT Network Service Systems Laboratories is developing the Secure ID Wallet, which provides a cloud-based wallet for storing digital identities equipped with a dedicated security module, as a countermeasure against these attacks and risks (Fig. 4). In the Secure ID Wallet, the wallet software is executed in an isolated execution environment on a server in the cloud using a hardware-implemented security module, such as a trusted execution environment (TEE)*5, to protect the memory content during the process as well as protect the persistence of the content by encrypting persistent data (confidentiality). If the software that implements the wallet is modified, even if the memory and data are encrypted, the data can be leaked or tampered with. Therefore, the wallet uses remote attestation*6, a mechanism that enables users to verify that the software has not been tampered with (integrity) from outside the system.
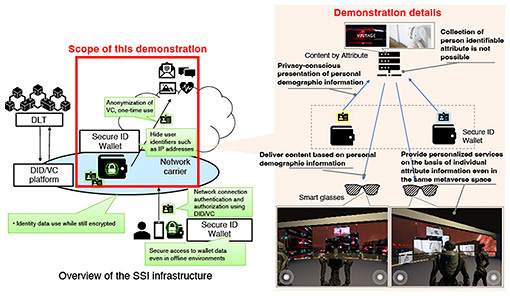
Another important issue is to ensure security when presenting digital identity information from a wallet to an external service. In addition to anonymization and one-time disclosure of DIDs in the data to be presented, technologies, such as selective disclosure, in which only the minimum attributes necessary for service use are disclosed out of the multiple attributes described in the digital identity information to be disclosed, are being considered and standardized. These technologies are useful for avoiding risks such as user profiling by name-dropping by service providers and leakage of privacy information. However, privacy risk measures are incomplete unless measures are taken not only for the information contained in the data but also for endpoint information such as the URL (Uniform Resource Locator) and IP (Internet Protocol) address used to access the user’s wallet. NTT Network Service Systems Laboratories is developing a one-time endpoint method and VC presentation method for not disclosing endpoint addresses to external services as a countermeasure against name identification of endpoint addresses in user wallets. To use the Secure ID Wallet more conveniently, we are also considering authentication linkage that enables secure and convenient connection to the Secure ID Wallet using information such as the authentication key recorded in the subscriber identity module (SIM) card inserted in the terminal owned by the user. We are also considering an integration function that works with other wallet services in anticipation of usage scenarios in which multiple wallets are used for different services. 5. Providing network services using digital identityWe now describe our study on the provision of network carrier services using digital identity information distribution. By digitizing identity information, service providers will be able to handle user identity information more dynamically and flexibly. Similarly, network connection service providers will be able to provide more flexible and diverse network connection services using users’ digital identity information. For example, the presented digital identity information can be used to identify urgent communications such as emergency vehicles, emergency calls, and medical services, and control the priority allocation of communication resources in the network. It is also possible that VCs can be used to implement a mechanism whereby other parties, such as service providers, bear the communication charges for communications used for specific services on behalf of users. Although these efforts are still in the research stage, NTT Network Service Systems Laboratories will continue to investigate ways to provide more convenient network services. 6. Use case demonstration with the metaverseNTT Network Service Systems Laboratories has been conducting demonstration tests to study the feasibility of the technologies introduced above in parallel with their research and development. A demonstration of the Inclusive Core using the metaverse as a use case was reported in a press release [5]. In this demonstration, we assumed a situation in which various service providers offer their services in the metaverse and need users’ personal information to provide personalized services tailored to each user. To prevent the leakage of privacy information beyond the necessary level, we applied the SSI infrastructure to a metaverse service and demonstrated that it is possible to personalize the content provided by the service provider by providing only the minimum necessary information (age information) from the user’s wallet. The user’s wallet is the aforementioned Secure ID Wallet. In addition to the data disclosed to the service provider, we implemented a method for avoiding the risk of user identification by making the endpoint information of the wallet one-time use. It also works with the In-network Service Acceleration Platform (ISAP)*7 that enables in-network computing in the Inclusive Core and implements a Secure ID Wallet on the ISAP to manage instances, demonstrating the ability to provide wallet services according to user locations and service usage conditions (Fig. 5).
7. Future outlookIn preparation for the full-scale launch of eIDAS 2.0 services in the EU in 2025, it is expected that the provision of digital identity-related services and development of digital identity-related technologies will accelerate worldwide. NTT Network Service Systems Laboratories will keep pace with these developments and continue to study standardization and technology establishment in cooperation with other telecommunications carriers to address various social issues through digital identity information distribution. References
|
|||||||||||||||||||||