|
|||||||||||||||||||||
|
|
|||||||||||||||||||||
|
Global Standardization Activities Vol. 23, No. 3, pp. 49–53, Mar. 2025. https://doi.org/10.53829/ntr202503gls Standardization Trends of Automated Intelligent Management for Access Systems in the Broadband ForumAbstractTo reduce operational costs in future access systems, research and development aimed at automating the network management and control by network operators is advancing. This article outlines the standardization of automated intelligent management for access systems within the Broadband Forum, highlighting the content that has been standardized thus far and providing an outlook on future developments. Keywords: automated intelligent management, network automation, SDN/NFV 1. Requirements for future access systemsAs the scale of networks expands, operating expense (OPEX) increases proportionally. Therefore, reducing OPEX has become crucial for telecommunications operators. In broadband services, in particular, network issues are often addressed based on customer complaints, making it essential to improve the efficiency of network maintenance and operations to reduce the operators’ workload. Network management and control are heavily reliant on individual experience and skills. With the anticipation of maintaining a vast number of network devices, such as those connected through Internet of Things, innovative solutions are needed to radically reduce the workload of telecommunications operators. The maintenance and management workload for home networks and access networks constitutes a significant portion of the overall maintenance and management efforts for end-to-end (E2E) services. Therefore, in future access systems, there is an expectation to automate the management and control of home and access networks to enhance maintenance and operational efficiency and reduce OPEX. 2. Overview of Broadband ForumThe Broadband Forum (BBF) is a global industry forum that promotes the adoption of broadband services and develops system management and control protocol specifications as well as interoperability specifications [1]. The BBF comprises over 150 companies and organizations, including service providers and system/chip vendors worldwide, and it has produced more than 200 Technical Reports (TR) to date. Figure 1 illustrates the organizational structure of the BBF. The Service Provider Action Council, shown in Fig. 1, is where service providers discuss and set the agenda and policies for the BBF. Based on these discussions, technical deliberations are conducted within various work areas that make up the technical committees tasked with developing specifications.
The BBF has focused on specifying various technologies for managing and controlling access systems that incorporate virtualization/componentization technologies such as software-defined network (SDN) and network functions virtualization (NFV). Among the access network standardization development organizations and industry organizations, the BBF is the most actively involved. It has been working on specifications for Network Configuration Protocol (NETCONF)*1/Yet Another Next Generation (YANG)*2 models for various access systems, virtualized architecture and interfaces for Cloud Central Office (CO)*3, specifications for the virtual ONU Management Control Interface (vOMCI) for managing and controlling virtualized optical network units (ONUs), and specifications for automated intelligent management (AIM) that automates management and control. This article introduces the specifications for AIM, which were completed as TRs in 2023.
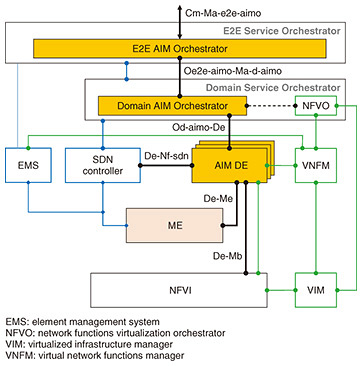
3. Specifications of AIMIn the BBF context, AIM has been specified as TR-436 “Access & Home Network O&M Automation/Intelligence” [2] and TR-486 “Interfaces for AIM” [3]. TR-436 specifies the architectural requirements for implementing AIM, while TR-486 specifies the interface requirements between the functional blocks that constitute the architecture. By applying this technology to the management and control of home and access networks, it is expected to automate processes traditionally carried out by operators, such as identifying the cause of communication failures and executing recovery. Additionally, it can automate the optimization of communication quality by reducing interference between different wireless local area networks. As this technology becomes a standard specification, it is anticipated that the full range of automation functions will be implemented efficiently and become widely used. 3.1 AIM architectureFigure 2 shows the reference architecture of AIM, created on the basis of TR-436. In AIM, the state and information of the managed entities (MEs) are collected, and appropriate settings are analyzed on the basis of predetermined policies in accordance with the changes in this information, thereby automating the management and control of the MEs. The main functional components for implementing AIM are as follows:
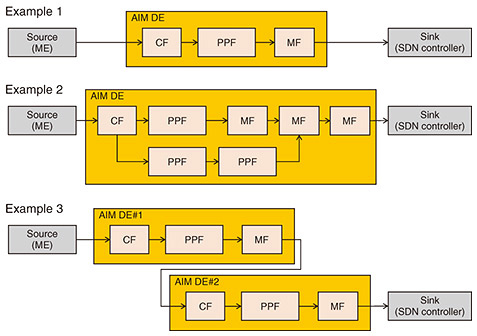
The analysis results (new settings) from the AIM DE are applied to the MEs through the SDN controller. The series of processes from collecting information from the MEs to executing control is referred to as a pipeline in AIM. The E2E AIM Orchestrator and Domain AIM Orchestrator are responsible for creating and managing these pipelines. The term “domain” represents the area controlled by a single AIM pipeline, which is defined abstractly in the specifications to allow for widespread application of the AIM architecture. For example, access networks, edge networks, and transport networks can each be regarded as domains, but the definition is not limited to these examples. Additionally, the specifications include methods for domain federation to achieve automated management and control not only within a single domain but also across multiple domains. We next explain the details of the AIM DE. The AIM DE is composed of a combination of sub-functions known as the collection function (CF), pre-processing function (PPF), and model function (MF). The CF is responsible for collecting status and information from the MEs. The PPF executes initial processing, such as filtering and statistical processing, on the collected data before analysis. The MF conducts analysis on the pre-processed collected data. Analysis methods include rule-based approaches, which make decisions on the basis of predefined logic, and machine-learning-based approaches, such as deep learning. Since the content of the PPF and MF depends on the desired automated management and control, specific implementations are not prescribed in the specification, allowing for a high degree of flexibility. Figure 3 shows example implementations of the AIM DE. As illustrated in the figure, each sub-function can be flexibly combined, and multiple AIM DEs can be connected, permitting versatile implementations. These sub-functions are implemented on the network functions virtualization infrastructure (NFVI) shown in Fig. 2.
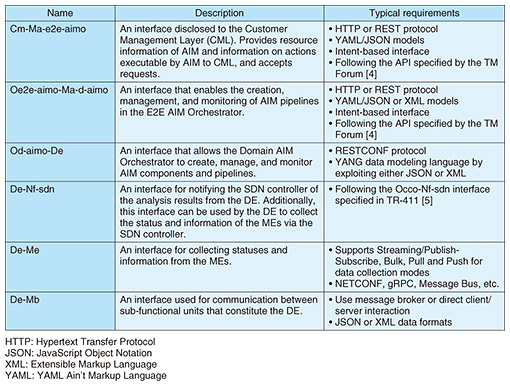
3.2 AIM interfacesTable 1 shows the AIM interfaces created on the basis of TR-486. The segments in which each interface is used are illustrated in Fig. 2. AIM interfaces are broadly categorized into management interfaces, which are used for generating, managing, and monitoring AIM pipelines, and pipeline interfaces, which are used as part of the AIM pipeline.
The following interfaces fall under management interfaces:
On the other hand, the following interfaces fall under pipeline interfaces:
As described in Table 1, management interfaces adopt the representational state transfer application programming interface (RESTful API)*4 or RESTCONF*5 as the protocol, which are common as programmable APIs. The pipeline interfaces, on the other hand, adopt NETCONF and gRPC (Google Remote Procedure Call), which was created to facilitate efficient inter-device communication, as protocols. While TR-486 specifies the protocols and data-modeling languages, it does not go so far as to specify concrete YANG data models. It is anticipated that future revisions will expand on this.
4. Future prospectsAs a latest topic in future access systems, we have introduced the standardization content of AIM within the BBF. Discussions on revising the specifications to enhance this technology are ongoing at the BBF. Specifically, these discussions include improving the completeness of domain federation features, extending functionalities to accelerate automated management and control, and expanding features from the perspectives of security and power saving. NTT will continue to participate in these efforts within the BBF and contribute to international standardization activities by presenting requirements as a telecommunications operator. References
|
|||||||||||||||||||||