|
|||||||||||||||||||
|
|
|||||||||||||||||||
|
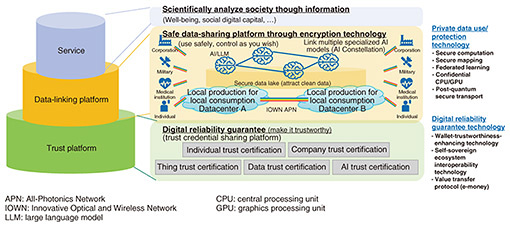
Feature Articles: Security R&D for a Better Future Vol. 23, No. 11, pp. 66–71, Nov. 2025. https://doi.org/10.53829/ntr202511fa8 Toward a Digital-data-enhanced Economy—Information Sharing Driven Using Digital Wallets for Individuals and EnterprisesAbstractWith a view to a digital-data-enhanced economy based on information sharing driven using digital wallets, NTT is researching and developing techniques for ensuring the trust in digital information, achieving encryption/decryption control, and enabling the secure and trusted use of digital data. On the basis of the three pillars of information authenticity, controllability, and security, we aim to develop platform technologies that will enable the use of trustworthy information that protects privacy through a digital identity wallet, decentralized trust, secure computation, etc. Keywords: digital trust, data governance, secure and trusted use of digital data 1. IntroductionA time in which all the information in the world will be digitized is fast approaching. Many human activities, such as shopping, moving about, medical care, education, and entertainment, are now being recorded as digital information in a way that shapes that set of information into our “other selves.” To use such a vast amount of information, a mechanism for sharing data securely while ensuring its trust is indispensable. However, problems exist, such as fake news, a flood of information due to generative artificial intelligence (AI), the hoarding of personal information, and the risk of privacy leaks. With a view to creating a digital-data-enhanced economy in which everyone can use their information and benefit from it, we are developing technology for ensuring trust in digital data together with encryption control and usage management, as the three pillars of trust platform, controllability, and confidentiality for digital data (Fig. 1) [1, 2].
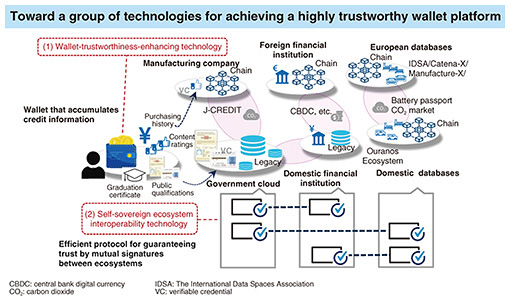
2. Making digital information trustworthyIf digital information is to become a social infrastructure, there is a need for technology that can guarantee its authenticity. We aim to construct a “trust-guaranteed next-generation Internet” that can guarantee the authenticity of the source and content of all types of information related to people, corporations, things, AI, data, etc. A trusted network across countries, industries, and corporations can thus be formed, enabling the secure sharing of information and value creation. We also aim to realize a digital identity wallet (DIW)*1 that can centrally record and manage all individual or corporate activities, transactions, etc. conducted in virtual space and real space. This type of wallet can be called an alter ego (digital twin), so to speak, of an individual or corporation. A variety of applications can thus be considered. For example, a personal AI assistant trained on this alter ego could come to understand one’s preferences and behaviors and make optimal proposals in terms of food, travel destinations, financial and health matters, etc. However, if such a DIW is to become widely used as a social infrastructure, how to ensure the authenticity and trust of the information stored in the wallet is a major issue. That is, if the information in the wallet cannot be trusted, the foundation for recommendations by a personal AI assistant, service linking, etc. will collapse, resulting in the trustworthiness of information sharing across all of society being lost. For this reason, we must systematically re-evaluate who is to possess, manage, and present trustworthy information, how is that to be done, and how can third parties verify that information? With this in mind, we have drawn up a three-step process for guaranteeing the authenticity of digital information. The first step is to give the information a certifiable format. This is because a mechanism is needed for sharing tamper-proof digital credentials such as the credential information, transaction proofs, and authentication results of individuals, corporations, service providers, and others. The validity of a digital credential’s content is guaranteed by the issuer’s signature. It is designed with a structure that enables the recipient to verify its authenticity and trustworthiness. The second step is to construct a mechanism that enables the user to autonomously manage and present that certification information. A DIW will play a central role for this. It is not simply a depository of information. Rather, it is a privacy-by-design platform in which the user can select and disclose appropriate certification information as needed. A DIW can provide both informational independence for individuals and ease-of-verification for service providers. The third step is the construction of a decentralized trusted platform*2 to support the issuer, verifier, and custodian of certification information. Verification of digital credentials requires a mechanism for storing and referencing an issuer’s public key, schema definition, revocation information, etc., but sharing a single root of trust throughout the world is difficult. We therefore believe that multiple trusted domains should be mutually interoperable with a structure that enables trusted relationships to be connected. Therefore, a global trusted network beyond nations and industries can be formed, enabling decentralized digital-credential sharing. To implement these three steps, we are developing two elemental technologies as platform technologies (Fig. 2).
The first is multi-party computation (MPC)-type wallet-trustworthiness-enhancing technology that applies secret-sharing technology. The secure management of private keys required for the presentation, signing, etc. of digital credentials is an element directly related to the trustworthiness of a DIW. However, a system that concentrates such keys on a single terminal or server is vulnerable to unauthorized access, data loss, and other problems. We therefore implement a mechanism that enables users to assign trusted individuals or other devices in key reconfiguration. This mechanism incorporates a social-recovery function in addition to MPC technology that divides a private key into multiple distributed elements and executes a signature in a collaborative manner. It thus achieves both security and convenience. The other elemental technology is self-sovereign ecosystem interoperability technology to facilitate cooperation between ecosystems. In contrast to a single, globally centralized registry, we aim for a structure that would enable mutual authentication and trust building between ecosystems independently constructed by countries or industries. Such a structure would enable diverse stakeholders to participate across different ecosystems and lead to the formation of a decentralized and pluralistic trusted network. Through the above steps and elemental technologies, we seek to create a world of digital information in which authenticity can be guaranteed. Such a world would not simply be one of enhanced security. Our aim is to develop a next-generation Internet platform that substantially redefines what trust means in the information society and enables everyone and AI to safely and efficiently coexist.
3. Controlling digital information as desiredThe situation with digital information is that, once it is out of the owner’s hands, they do not know how it will be used. In essence, digital information is something that should be managed independently by the owner, so a mechanism that can guarantee that data are processed according to the owner’s expectations is indispensable. In response to this issue, NTT is researching and developing functions such as policy-based access control, visualization of information usage history, and certification/verification by third parties as a mechanism that would enable users to control how their information is used. We also aim to achieve true data governance*3 through a design that prevents information within a DIW from being leaked to others and by constructing a mechanism that would prevent even NTT as the platform operator from accessing data content owned by individual users. This would provide a foundation for sharing information in a secure and trustworthy manner and for benefiting from that information through AI or other means. Data governance as viewed by NTT means that users can control the use of their digital information even if that information is out of their direct control. This raises the question: what constitutes a state of data governance? Data are repeatedly subjected to a variety of processes such as accumulation, transmission, and calculation throughout their lifecycle from their original creation to extinction (deletion). In data governance as conceived by NTT, there are two requirements: data must always be in an encrypted state throughout such processes, and opportunities for viewing, processing, duplicating, reusing, etc. the data by parties other than the person authorized to use those data must be minimized. In other words, it is not only necessary to prevent access by attackers with malicious intent but also to minimize opportunities for unintended data acquisition by parties having no appropriate authorization. This requires that data to be always in encrypted form other than in situations where the data are needed, thus creating a world of confidentiality, i.e., a world with no plain text. This means, for example, that data must be consistently encrypted throughout their lifecycle and their decoding allowed only by parties approved by the user in cases based on approved conditions, a framework that enables data to be analyzed and processed in a ciphertext state must be established, and the use of processing results on the basis of those data must be limited to conditions approved by the user. In NTT’s view of data governance, a platform equipped with functions that can appropriately manage such data usage, including external computing platforms such as cloud services and datacenters built on those computational platforms, can be regarded as a state in which data are securely stored in a vault. That is, a state in which the security of the platform can be proven by the relevant party or third parties such as auditors or, a state within a computing space in which data are appropriately protected with cryptographic technology and rights management. Data governance as conceived by NTT is achieved with a combination of technologies described above. The following outlines two of these key technologies: certification/verification by third parties and preventing information from being leaked to others or from being accessed by NTT. Certification/verification by third parties proves—in a verifiable manner by the concerned party or third parties—that a system involved in data sharing is appropriately designed, constructed, and operated. For example, when connecting a certain system to another system for sending/receiving sensitive data, how can either of those systems trust the other system and how can it be determined that data sending/receiving is being appropriately done? One way of doing so would be to periodically conduct an external audit and have a third party grant a seal of approval indicating that the system is appropriately designed, constructed, and operated. This approach, however, is limited in terms of the degree of authenticity that can be guaranteed. In contrast, NTT has proposed an approach called mutual attestation*4. “Attestation” means that a certain system (software, hardware, settings, etc.) is legitimate and in a non-tampered state. For example, attestation can be used to determine whether two systems that are trying to connect to each other can mutually trust each other by using measured values (attestation values) that shows that a specific version of an operating system or application is running. Preventing information from being leaked to others or from being accessed by NTT aims to guarantee that data are consistently managed and applied in an encrypted state from their creation to deletion. This design stipulates that data decryption is to be executed at a bare minimum of times and that decrypted data (so-called raw data) are to be disclosed to a bare minimum of parties with a bare minimum of authority. Thus, unintended provision of data to others and the risk of leaks to others via the data recipient can be reduced as much as possible. To give a specific example, NTT has proposed a framework called Confidential Remote CPU/GPU (CPU: central processing unit, GPU: graphics processing unit). This framework combines confidential computing*5 technology centered on a trusted execution environment (TEE), which is a secure processing environment featuring hardware-wise isolation within a CPU and memory encryption, and post-quantum secure transport technology [3] centered on an end-to-end network-encryption function for achieving advanced attack resistance and high availability in the quantum computer era. This configuration will protect confidential computing spaces via a post-quantum secure network by implementing a network-connection function using post-quantum secure transport technology in each virtual machine in a TEE confidential computing environment. It will thus be possible to securely connect multiple, separately installed confidential computing environments at the communications level. On the basis of the concept of distributed datacenters, we can consider how Confidential Remote CPU/GPU technology could be used to virtually integrate multiple confidential computing spaces omnipresent in multiple datacenters mutually connected by the All-Photonics Network (APN) of NTT’s high-speed, high-capacity, and low-latency Innovative Optical and Wireless Network (IOWN). These virtually integrated computing spaces could then be used as a single, large-scale confidential computing space. In the future, centered, for example, on model generation in AI, we can expect heightened demand for far more data than currently available by processing data in far more advanced computing environments and generating new data. By advancing the social implementation of technologies related to the use of digital information centered on the above two technologies, NTT aims to enable advanced and secure use of digital information with data governance guaranteed.
4. Secure use of digital informationIf digital information can be shared throughout society, we can expect the creation of shared knowledge on a more abundant level. At that time, however, issues related to privacy and confidentiality must be simultaneously overcome. We are developing a mechanism for using information without showing it by applying advanced technologies such as secure computation*6, federated learning, and secure matching. In a society capable of using information without showing it, all kinds of information can be securely shared in an encrypted state at all times and individuals and organizations can provide and analyze information without having to rely on trust and consent. We aim to achieve such a society, and as a mechanism for doing so, we are developing an information-sharing platform. In such an ideal society, information confidentiality and provider privacy can be technically guaranteed even in the process of using information. This will enable secure sharing of knowledge and the creation of abundant shared knowledge. Information security is currently supported by the legal system, and security is protected by laws including the Act on the Protection of Personal Information in Japan. Thus, the handling of sensitive information involves, for example, clarifying the purpose of use, obtaining the consent of the person concerned, and taking thorough security-management measures. However, obtaining the consent of the information provider and implementing security management and auditing procedures within an organization can be costly and labor intensive. This can become a major barrier to using information particularly in data linking among multiple organizations, wide-area analysis, etc. To overcome these issues, efforts are being made to guarantee and supplement security demanded by the system through technical means. Instead of relying solely on formal trust based on law, this approach attempts to achieve security that prevents the risk of leaks from occurring in the first place. However, achieving such an ideal information society any time soon is difficult. More time and a stepwise approach are needed to set up a legal framework, obtain social acceptance, implement advanced technologies that are accompanied by high computational costs, etc. The use and application of statistical information is one field in which the implementation of security by technical means is progressing relatively early. In particular, the social implementation of technology for processing data without identifying personal information and using those data for analysis and decision-making in conformance with the legal system is becoming a reality. As the first step in this stepwise effort, secure computation, for example, is attracting attention as a technology that could be implemented. Technologies such as secure computation are capable of processing data without having to show those data, thus they hold the key to minimizing legal and ethical risks. Going forward, it is essential that these technologies be enhanced and that we cultivate understanding and trust from the legal system and society overall.
5. Toward the creation of a digital-data-enhanced economyAdvanced social optimization as in early detection of illnesses, prediction and easing of traffic jams, and reduction of food loss can be achieved by having medical institutions, local governments, transportation companies, and other entities combine and match up their data. To achieve a society of mutual understanding that connects people and people and people and communities on the basis of trust, we are researching a mechanism for achieving trustworthy information sharing. A digital-data-enhanced economy that makes the world a true digital society—that is, a society in which everyone can use their information to make high-value choices—is the form of information sharing driven using digital wallets that we are targeting. References
|
|||||||||||||||||||